Some of the most devastating cyberattacks don’t rely on brute force, but instead succeed through stealth. These quiet intrusions often…
Malware isn’t just trying to hide anymore—it’s trying to belong. We’re seeing code that talks like us, logs like us,…
Cybersecurity researchers are calling attention to a new wave of campaigns distributing a Python-based information stealer called PXA Stealer. The…
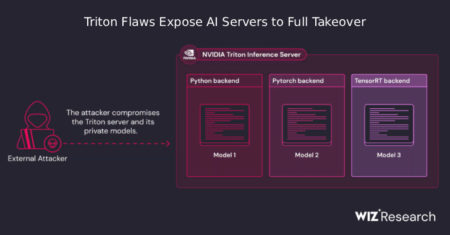
A newly disclosed set of security flaws in NVIDIA’s Triton Inference Server for Windows and Linux, an open-source platform for…
Understanding how users think, behave, and interact with your product isn’t optional, it’s a strategic necessity. UX research methods help…
In the past, when the idea of computers graphically representing the result of a user’s actions before printing seemed like…
Swedish design is world-renowned for its clean lines, minimalist approach, and functional beauty, and that same philosophy shines through in…
Duolingo’s Math team ditches traditional handoff in favor of co-creation, scrappy prototypes, and constant experimentation. Source: Read MoreÂ
As always, we’re keeping an eye on the latest tools making life easier for our fellow developers. In this post,…
Before the logo, the website, or the color palette gets approved, there’s the mood board. It’s where early ideas start…
Node.js has undergone a remarkable transformation since its early days. If you’ve been writing Node.js for several years, you’ve likely…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
The Shift-Right approach is rapidly becoming a cornerstone of modern quality engineering, offering enterprises a smarter way to ensure software excellence post-deployment. Unlike the traditional Shift-Left model, which focuses on early testing in the development lifecycle, Shift-Right emphasizes continuous validation in production using real-user data and behavior insights. This strategy helps organizations improve customer experience, resolve issues faster, and make data-informed decisions with greater precision. Read the blog now
The post Shift-Right Testing Isn’t Optional Here’s How AI and Real Users Are Making It Work first appeared on TestingXperts.
Please keep in mind, I’m just trying to get points so I can join a particular group. I need 20. But if you feel like you could give a decent answer, I’m all ears.
The code architecture thing being bugless is more of me perusing through stack exchange and seeing so many “How come when I do this this happens” or “when I place this and I’ve been doing it for years. This happens but I can’t do it now with this new thing?”
It seems like a lot of of stuff not working cuz they’re no longer compatible or something’s “flipped” incorrectly or needs to be “connected” to the correct calibrator (I’m sure I’m saying gibberish), but the idea is essentially the same. Why are there so many tiny technical incompatibilities? Isn’t there some form of architecture that just limits this or makes it impossible to happen?
Someone should get on that (I ask ignorantly)
Just curious: I’ve always written tests in a declarative style especially with page object model. But doesn’t this break the single responsibility principle? I used to write things with an imperative style but maintenance was a headache and it was harder to read.
So my question is: Is there a general consensus of which we should be using in our tests? And if it IS declarative, doesn’t that break SOLID (specifically the S) principles?
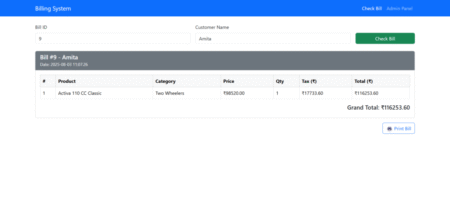
The Billing System using PHP and MySQL is a role-based application designed to streamline and automate the process of billing…
Satya Nadella admits Microsoft’s 15k layoffs “weigh heavily” on him even as the stock tops $500, exposing the uneasy trade-off…
Google has launched Opal in Google Labs (U.S. only), letting sketch web apps with simple text prompts and tweak each…
Fantasy Premier League teams get Copilot’s picks and Firefly’s custom kits as Microsoft and Adobe drive the next phase of…