Meta is seemingly having a hard time keeping its relatively new employees despite multimillion-dollar offers, with several members jumping ship…
Instead of ray tracing, Battlefield 6 doubles down on optimization, giving players high FPS, broad accessibility, and better stability across…
The US now owns 9.9% of Intel and wants the chipmaker to retain control of its foundry business. Source: Read…
CDKeys is officially rebranding as Loaded, but gamers have had a mixed response so far. Source: Read More /
Helldivers 2’s CEO says split-screen co-op is “technically feasible” and even 8-player lobbies could be possible, as the game surges…
Winux is a Linux operating system heavily inspired by Windows 11 and 10, from the Start menu to desktop icons…
Salesforce CEO Marc Benioff recently revealed that he scaled down the company’s support staff from 9,000 to 5,000 due to…
Microsoft’s next flagship Surface Pro is in development. Here’s everything we think we know, and what we want to see…
Windows 11 now delivers super wideband stereo audio over Bluetooth, improving game chat, Teams calls, and voice apps with clearer,…
Genshin Impact 6.0 Luna I launches September 10 with Nod-Krai, new mechanics, characters, and free 5★ anniversary rewards. Source: Read…
Voyagers transforms No Man’s Sky with buildable, walkable starships, new multiplayer features, and shared interiors. The update, powered by Light…
Microsoft’s $3.1B deal with the US government brings free Copilot, Azure discounts, and waived data fees to federal agencies for…
PlayStation and Xbox have been playing nice this summer, and this latest sales milestone might be a good indicator for…
Sledgehammer Games’ Call of Duty: WWII was added to the Microsoft Store at the end of June, only to be…
Blue Prince is getting a stunning physical edition packed with collectibles — but it’s exclusive to PS5. Despite the game’s…
Ubisoft’s Rayman series could be making a return, with a Rayman remake reportedly in development and targeting a late 2026…
Learn how to convert MBR to GPT, switch BIOS to UEFI, and enable TPM 2.0 and Secure Boot on Windows…
Windows hotkey conflicts can be frustrating, but PowerToys v0.94 adds conflict detection to help you spot and fix clashing shortcuts.…
The exciting release of Helldivers 2’s Into the Unjust update has been marred by severe bugs and performance issues introduced…
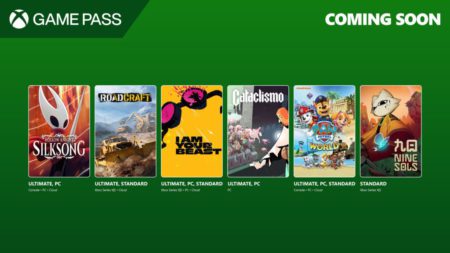
Xbox Game Pass kicks off September 2025 with Hollow Knight: Silksong, RoadCraft, PAW Patrol World, and more. Here’s the full…