Amazon Q Business is a fully managed, generative AI-powered assistant that helps enterprises unlock the value of their data and…
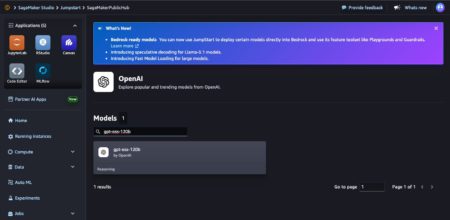
Today, we are excited to announce the availability of Open AI’s new open weight GPT OSS models, gpt-oss-120b and gpt-oss-20b,…
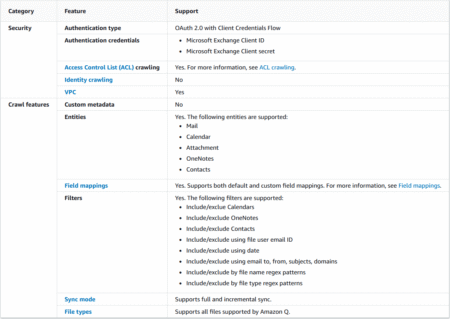
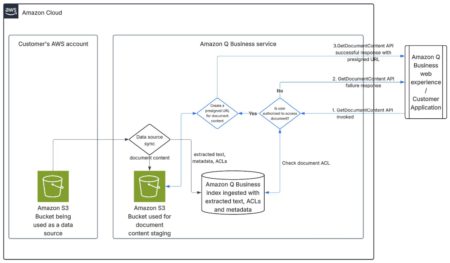
Organizations need user-friendly ways to build AI assistants that can reference enterprise documents while maintaining document security. This post shows…
If you’re reading this article on the freeCodeCamp publication, you should see some visual clues in different sections of the…
Meet Acquia Source Acquia Source powered by Drupal is Acquia’s SaaS solution to streamline building, managing, and deploying websites at…
In the face of economic uncertainty, shifting buyer expectations, and rapid technological change, manufacturing marketers must evolve to stay competitive.…
As people who live in the information age, we often have to give up our privacy to use collaboration tools…
I am helping my child learn coding. No, not the new born, but “my favorite child”, Ushika, who is now…
SonicWall said it’s actively investigating reports to determine if there is a new zero-day vulnerability following reports of a spike…
To protect digital privacy, the UAE Cybersecurity Council has issued a strict warning against the use of unofficial and unverified…
Cybersecurity researchers have lifted the veil on a widespread malicious campaign that’s targeting TikTok Shop users globally with an aim…
Why do SOC teams still drown in alerts even after spending big on security tools? False positives pile up, stealthy…
In SaaS security conversations, “misconfiguration” and “vulnerability” are often used interchangeably. But they’re not the same thing. And misunderstanding that…
Cybersecurity researchers have disclosed a high-severity security flaw in the artificial intelligence (AI)-powered code editor Cursor that could result in…
Google has released security updates to address multiple security flaws in Android, including fixes for two Qualcomm bugs that were…
In episode 62 of The AI Fix, your hosts learn how AI models smash through CAPTCHA roadblocks like they’re made…
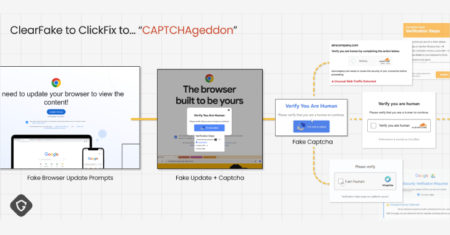
A combination of propagation methods, narrative sophistication, and evasion techniques enabled the social engineering tactic known as ClickFix to take…
Your goal is not to write a book, it’s to change how your reader thinks Source: Read More
Post Content Source: Read MoreÂ
In Agile software development, the demand for high-quality test data is crucial, but traditional production data often leads to bottlenecks due to privacy and compliance concerns. Synthetic test data, generated by AI, offers a secure, flexible alternative by mimicking real data without exposing sensitive information. It speeds up testing, improves coverage, and uncovers edge cases missed by traditional data. With synthetic data, teams can quickly generate tailored datasets for each test scenario, reducing waiting times and improving efficiency. Embracing synthetic test data helps businesses accelerate delivery, enhance product quality, and innovate faster.
The post Break Free from Legacy Bottlenecks – How Synthetic Test Data Fuels Agile Innovation first appeared on TestingXperts.