Bloober Team has recently uploaded a developer diary for its upcoming sci-fi horror game, Cronos: The New Dawn, which delves…
A Lenovo Clearance Sale is currently going on, and many of these devices are perfect for students heading back to…
I’ve been using the Lenovo Legion Tower 7i (Gen 10), and while it isn’t a massive departure, it’s a better…
OpenAI has restored GPT-4o for ChatGPT following backlash — but the warmer, more personable model is now paywalled. Source: Read…
AI is far more than the likes of ChatGPT and Copilot, and while these online tools are accessible to all,…
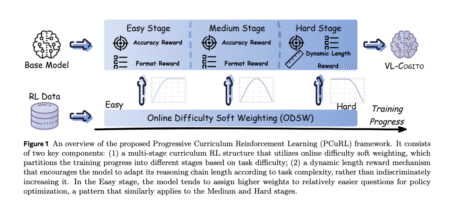
Multimodal reasoning, where models integrate and interpret information from multiple sources such as text, images, and diagrams, is a frontier…
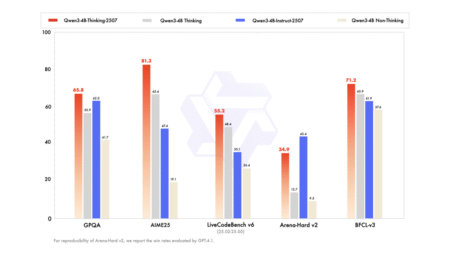
Smaller Models with Smarter Performance and 256K Context Support Alibaba’s Qwen team has introduced two powerful additions to its small…
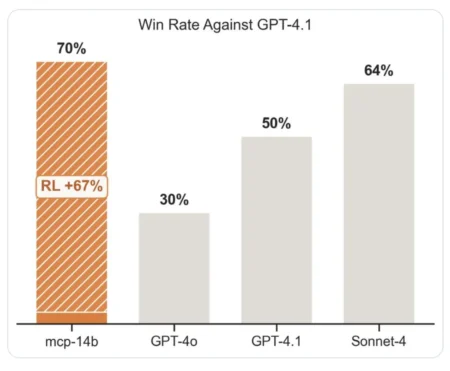
Table of contents Introduction What Is MCP- RL? ART: The Agent Reinforcement Trainer Code Walkthrough: Specializing LLMs with MCP- RL…
Table of contents TL;DR 1) What is an AI agent (2025 definition)? 2) What can agents do reliably today? 3)…
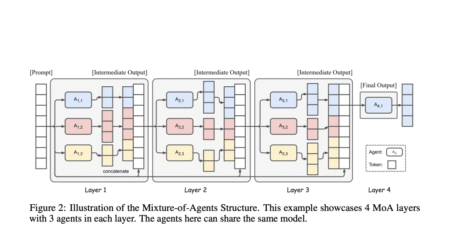
The Mixture-of-Agents (MoA) architecture is a transformative approach for enhancing large language model (LLM) performance, especially on complex, open-ended tasks…
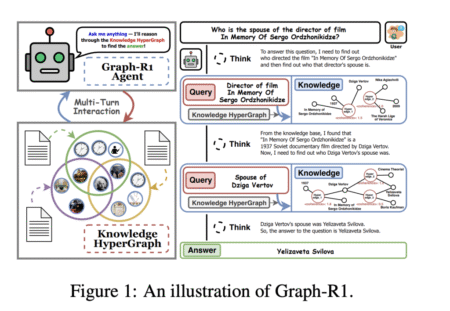
Introduction Large Language Models (LLMs) have set new benchmarks in natural language processing, but their tendency for hallucination—generating inaccurate outputs—remains…
In this tutorial, we walk through building an advanced PaperQA2 AI Agent powered by Google’s Gemini model, designed specifically for…
Table of contents Why Classic AI Agent Workflows Fail The 9 Agentic Workflow Patterns for 2025 Sequential Intelligence Parallel Processing…
Is your phone suddenly flooded with aggressive ads, slowing down performance or leading to unusual app behavior? Here’s what to…
A sky-high premium may not always reflect your company’s security posture Source: Read More
Cybersecurity researchers have discovered over a dozen vulnerabilities in enterprise secure vaults from CyberArk and HashiCorp that, if successfully exploited,…
Cybersecurity researchers have uncovered a jailbreak technique to bypass ethical guardrails erected by OpenAI in its latest large language model…
Cybersecurity researchers have disclosed vulnerabilities in select model webcams from Lenovo that could turn them into BadUSB attack devices. “This…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ