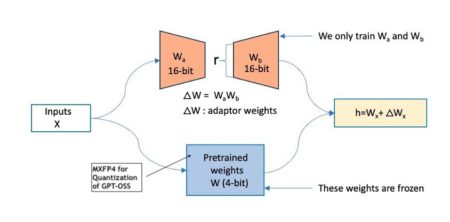
Released on August 5, 2025, OpenAI’s GPT-OSS models, gpt-oss-20b and gpt-oss-120b, are now available on AWS through Amazon SageMaker AI…
“How much will it cost to run our chatbot on Amazon Bedrock?” This is one of the most frequent questions…
Embodied AI agents that can perceive, think, and act in the real world mark a key step toward the future…
NuMind AI has officially released NuMarkdown-8B-Thinking, an open-source (MIT License) reasoning OCR Vision-Language Model (VLM) that redefines how complex documents…
In this tutorial, we walk through building a compact but fully functional Cipher-based workflow. We start by securely capturing our…
Corpus Aware Training (CAT) leverages valuable corpus metadata during training by injecting corpus information into each training example, and has…
Discover some of the interesting features that have landed in stable and beta web browsers during July 2025. Source: web.dev:…
Read about various happenings with Baseline during July 2025. Source: web.dev: BlogÂ
Baseline information is now available for CSS properties in the Elements panel of Chrome DevTools! Source: web.dev: BlogÂ
For most of people, JavaScript still conjures images of simple web interactions like toggling menus, validating forms, or animating buttons.…
Introduction: The Evolution from Automation to Intelligence Imagine a world where your software tools don’t just do what you tell…
In earlier blogs – Why AI-Led Experiences Are the Future — And How Sitecore Stream Delivers Them and Creating a…
John Henry and the AI Age: When the Hammer Meets the Algorithm What if winning against the machine still meant…
The maintainers of the WinRAR file archiving utility have released an update to address an actively exploited zero-day vulnerability. Tracked…
A new class of USB-based attacks has come to light. These attacks are not just targeting removable devices, but existing,…
Xerox Corporation has issued urgent security updates addressing two high-impact vulnerabilities in its FreeFlow Core software. The flaws, now tracked…
The Evolution of Exposure Management Most security teams have a good sense of what’s critical in their environment. What’s harder…
This week, cyber attackers are moving quickly, and businesses need to stay alert. They’re finding new weaknesses in popular software…
Malicious actors have been observed exploiting a now-patched critical security flaw impacting Erlang/Open Telecom Platform (OTP) SSH as early as…
Cybersecurity researchers have discovered a fresh set of security issues in the Terrestrial Trunked Radio (TETRA) communications protocol, including in…