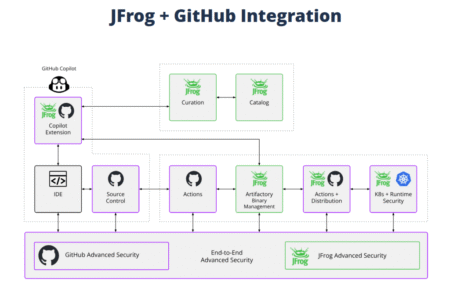
Today, we’re introducing a new integration between GitHub and JFrog that connects your source code and your attested binaries in…
Grenoble-based Scintil Photonics, a company developing integrated Photonic System-on-Chip (PSoC) solutions for AI infrastructure, has closed a $58 million Series…
Elon Musk’s idea of a humanoid robot army that outnumbers humans is raising questions about the future of work. Source:…
Espoo-based Agate Sensors, a startup developing smart sensors for material analysis, has raised €5.6 million. The funding will help commercialise a…
Chops was a developer for Initrode. Early on a Monday, they were summoned to their manager Gary’s office before the…
The blog discusses how Multi-Agent Systems (MAS) are transforming test automation by replacing brittle, linear scripts with adaptive, intelligent agents. From faster feedback to scalable pipelines, MAS enables QA teams to match the pace of DevOps with improved resilience, automation, and collaboration.
The post Leading the QA Charge: Multi-Agent Systems Redefining Automation first appeared on TestingXperts.
Discover SmythOS, the open-source operating system for AI agents. Move from fragile prototypes to production-ready multi-agent systems with proper orchestration,…
Navigation is one of the most important parts of any mobile application. Users expect to move seamlessly between screens such…
Postman is a platform used by developers, API testers, technical writers and DevOps teams for testing, documenting and collaborating on…
The iOS App Store submission process can feel like a daunting maze, but it doesn’t have to be. We just…
Imagine that you’re sipping a hot latte from Starbucks on your way to work. You quickly swipe your card, and…
As a dev, you’d probably like to write your application once and not have to worry so much about where…
The biggest bottleneck in most business workflows isn’t a lack of data; it’s the challenge of extracting that data from…
Comments Source: Read MoreÂ
As artificial intelligence continues to reshape the digital landscape, organizations are seeking clarity on how to strategically integrate AI into…
We’re proud to share that Perficient’s What If? So What? podcast has been named a Gold Stevie® Award winner in…
Financial services leaders are turning our 2025’s top digital payments trends into reality—from leveraging AI for smarter decision-making to embedding…
While the industry is racing to develop and implement artificial intelligence into its systems, cultural resistance, a skills gap, and…
Australia’s Qantas Airways has announced a cut in short-term incentives for its Group CEO and executive team following a major…
The UAE Cyber Security Council (CSC) has issued a stark warning that 70 per cent of smart home devices are…