Hacktivists claimed breaching the network of Belarusian intelligence agency and allegedly leaked their data in response to the intelligence chief’s…
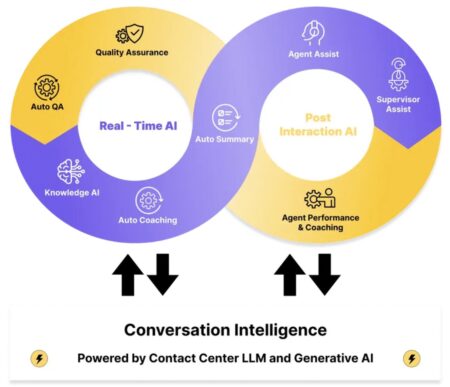
What’s really happening in your business? The answer to that question lies in the millions of interactions between your customers…
Software development with Continuous Integration and Continuous Delivery(CI/CD) is quite essential tool for gaining automation, speed up, and reliability of…
Cloud migration consulting is crucial for businesses looking to enhance operational efficiency, security, and scalability in the digital realm. The blog discusses how a cloud migration consultant is key in planning and executing a smooth transition to cloud platforms, utilizing deep expertise to optimize infrastructure and operations. From risk management to cost-effectiveness, consultants ensure a seamless integration of cloud technology, aligning it with long-term business goals. Their support mitigates risks, reduces costs, and minimizes downtime, paving the way for a successful digital transformation.
The post Why is Cloud Migration Consulting Important for Businesses? first appeared on TestingXperts.
Unlocking Efficiency: A Guide to Intercompany Reconciliation Software Modern businesses, with the predominance of remote work and globalised operations, often…
The Top Credit Card Reconciliation Softwares in 2024 Credit card reconciliation is a crucial aspect of financial management for businesses…
Imagine you’re a financial manager at a bustling enterprise, entrusted with the responsibility of ensuring the accuracy and integrity of…
The notorious Hunters group has allegedly added two new victims to their dark web portal: Rocky Mountain Sales in the…
A threat actor purports to be selling the database of the Central Bank of Argentina on a hackers’ forum. The…
The threat actor USDoD claimed that they had published the Personally Identifiable Information (PII) of about 2 million members of…
Multiple critical security flaws have been disclosed in the Judge0 open-source online code execution system that could be exploited to obtain code execution on…
Okta reported an “unprecedented scale” of credential stuffing attacks targeting its identity and access management solutions, resulting in the breach…
If you’re a designer, you know how important it is to have a library of resources that can help you…
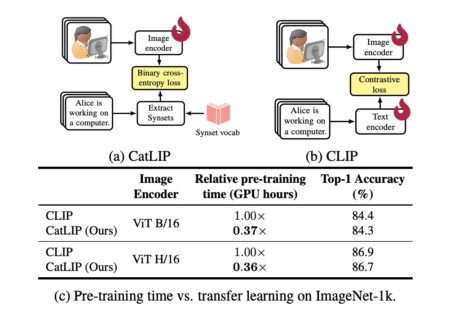
In recent times, contrastive learning has become a potent strategy for training models to learn efficient visual representations by aligning…
A group of researchers in France introduced Dr.Benchmark to address the need for the evaluation of masked language models in…
As businesses increasingly rely on data-driven decision-making, the ability to extract insights and derive value from data has become quite…
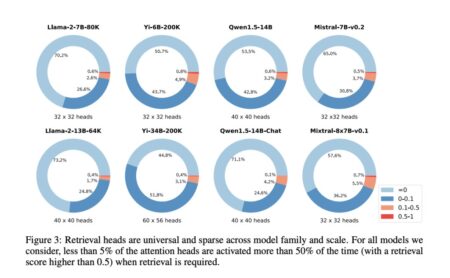
In computational linguistics, much research focuses on how language models handle and interpret extensive textual data. These models are crucial…
The notorious NoName ransomware group this time has allegedly set its sights on Moldova, targeting key government websites in what…
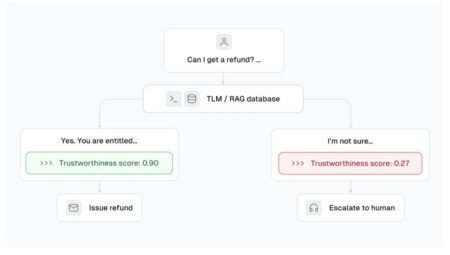
While 55% of organizations are experimenting with generative AI, only 10% have implemented it in production, according to a recent…
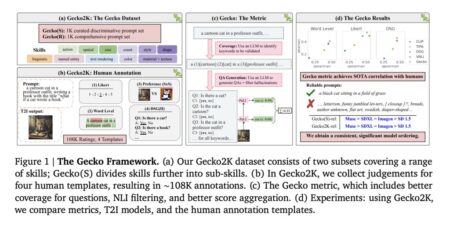
Text-to-image (T2I) models are central to current advances in computer vision, enabling the synthesis of images from textual descriptions. These…