How to Use a PHP GitHub Webhook Package to Automatically Update the Code of an Application When the Code Changes…
One time passcode Vue 3 Input Component. Continue reading on Vue.js Feed » Source: Read More
The Play ransomware group has claimed responsibility for an attack on the Kansas City Scout System which forced its staff…
Data sourced from over 40 million exposures that pose high-impact risks to numerous critical business entities revealed that Active Directory…
A Russian operator of a now-dismantled BTC-e cryptocurrency exchange has pleaded guilty to money laundering charges from 2011 to 2017. Alexander Vinnik,…
Google on Monday announced that it’s simplifying the process of enabling two-factor authentication (2FA) for users with personal and Workspace…
The RSA Conference 2024, the world’s biggest cybersecurity event, is currently underway at the Moscone Center in San Francisco. Over…
How safe is your comments section? Discover how a seemingly innocent ‘thank you’ comment on a product page concealed a…
The U.S. Secretary of State Antony Blinken unveiled an International Cyberspace and Digital Policy Strategy on Monday, outlining the Biden…
The personal data of an unspecified number of active UK military personnel had been compromised in a significant Ministry of…
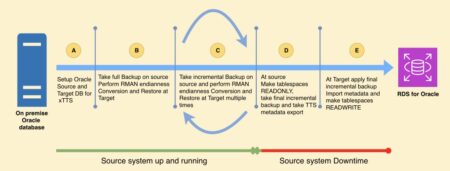
Organizations want to move their critical Oracle workloads to Amazon Relational Database Service (Amazon RDS) for Oracle with minimal downtime…
To remove some of the confusion, here’s a list of misconceptions about Specificity in CSS Source: Read MoreÂ
If we’re being honest with ourselves, the transformative new era hasn’t been so transformative yet. We were given the ‘most profound technology since…
Today, we’re back with some nice design finds: hover effects on images. These effects enhance images by revealing additional details…
One in three consumers (32%) will abandon a brand they love after a single poor experience. Designers can’t afford bad…
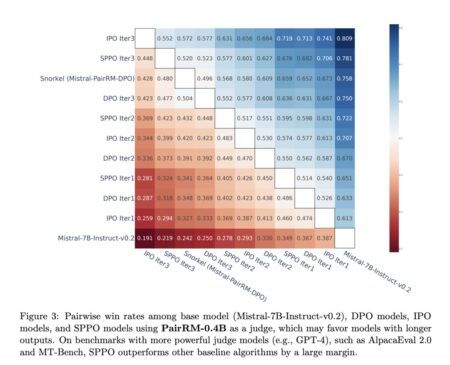
Large Language Models (LLMs) have demonstrated remarkable abilities in generating human-like text, answering questions, and coding. However, they face hurdles…
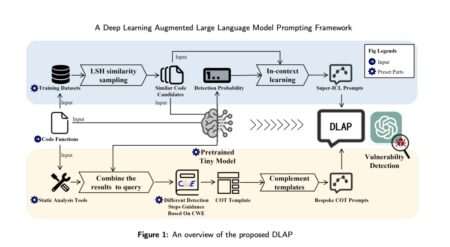
Software vulnerability detection is a critical field focused on safeguarding system security and user privacy by identifying security flaws in…
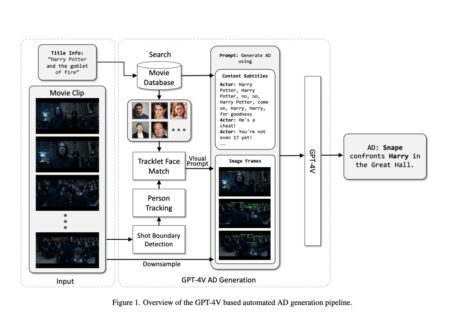
The introduction of Audio Description (AD) marks a big step towards making video content more accessible. AD provides a spoken…
Reinforcement learning (RL) is a fascinating field of AI focused on training agents to make decisions by interacting with an…
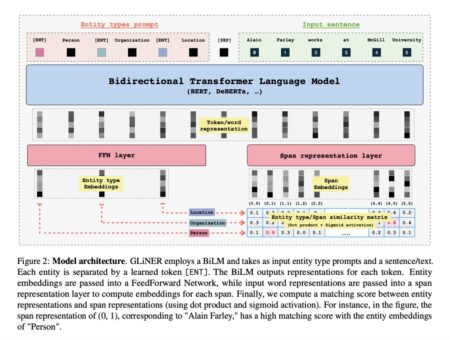
A key element of Natural Language Processing (NLP) applications is Named Entity Recognition (NER), which recognizes and classifies named entities,…