An INTERPOL-coordinated operation, dubbed Operation Serengeti 2.0, delivered a telling blow to cybercrime across the African continent. The operation that ran between June and August, this year, saw 1,209 arrests made across 18 African nations and the UK, while 11,432 malicious online infrastructures, including domains, IPs, and phishing or C&C servers, seized.
Financially, investigators recovered US$97.4 million tied to ransomware, business email compromise and online scams.

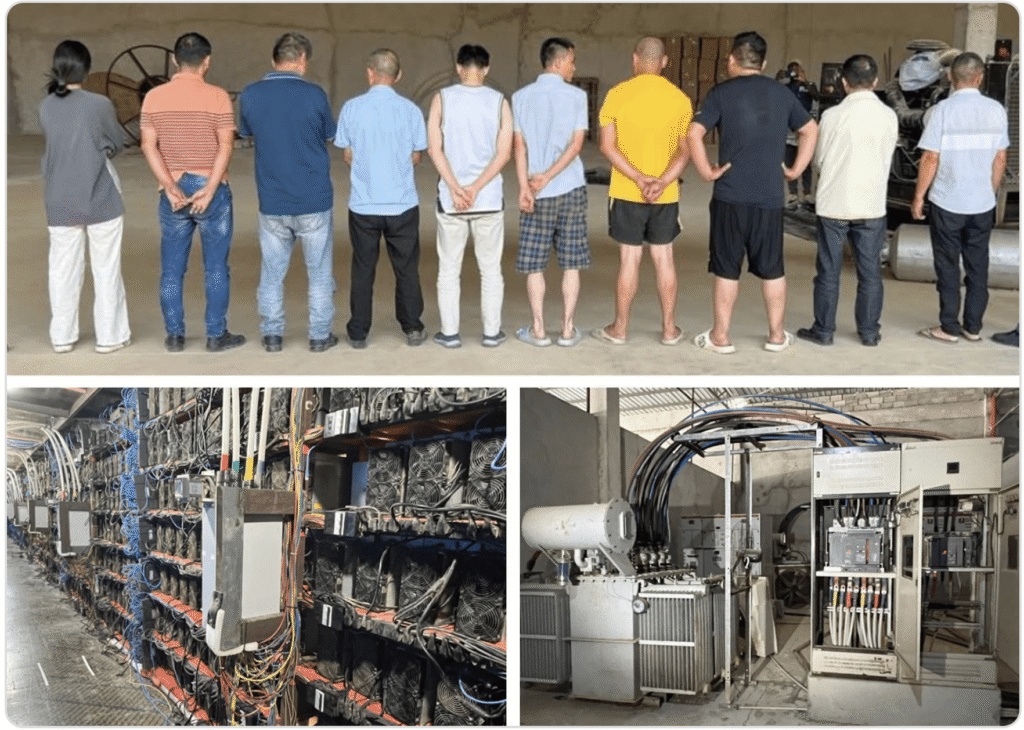
In Angola, authorities dismantled 25 illegal cryptocurrency mining centers run by 60 individuals, along with 45 illicit power stations and related hardware collectively worth $37 million.
Meanwhile, in Zambia, an audacious investment scam duped 65,000 individuals of approximately $300 million. This bust of the scam ring led to the arrest of 15 individuals and confiscation of key digital assets, including domain names and mobile accounts.
Côte d’Ivoire, meanwhile, targeted a transcontinental inheritance scam tied back to Germany, seizing assets such as electronics, jewelry, cash, and vehicles after defrauding victims of $1.6 million.
Private Sector Intelligence Fueling Real-Time Action
Crucial to the operation’s impact was intelligence sharing from the private sector, acting as an INTERPOL Gateway partner. The prior mapping of investment and BEC infrastructures of these threat intelligence companies and the preparatory workshops they conducted on OSINT and dark web tracking bolstered investigator readiness across jurisdictions.
Operation Serengeti 2.0 reveals why cybercrime in Africa has evolved from low-volume fraud to a continent-spanning economy of digital extortion. The success of the operation is built on the continuous efforts that led to the arrest of nearly 1,000 individuals in the first round of sweeping arrests.
Read: Major Cybercrime Operation Nets Over 1,000 Arrests Across Africa
The outcomes—mass arrests, dismantled infrastructure, and financial restitution—demonstrate what can happen when law enforcement, industry, and international partners move with coordinated precision. For organizations globally, it’s a blueprint – dismantling cybercrime requires intelligence-driven, multilateral collaboration.
Source: Read More