A new HTTP/2 denial of service (DoS) vulnerability that circumvents mitigations put in place after 2023’s “Rapid Reset” vulnerability is largely being addressed by affected vendors and projects, thanks to responsible disclosure by the researchers who discovered the flaw.
The new HTTP/2 DoS vulnerability, CVE-2025-8671, was publicly disclosed by Tel Aviv University researchers on Aug. 13, but the researchers have apparently been working with vendors since May to mitigate the flaw.
According to a Cloudflare blog post, the vulnerability exists only “in a limited number of unpatched HTTP/2 server implementations that do not sufficiently enforce restrictions on the number of times a client may send malformed frames.”
New HTTP/2 DoS Vulnerability Dubbed ‘MadeYouReset’
Gal Bar Nahum, who discovered the flaw along with fellow Tel Aviv University researchers Anat Bremler‑Barr and Yaniv Harel, said in a blog post that the flaw “lets an attacker create effectively unbounded concurrent work on servers by bypassing HTTP/2’s built-in concurrency limit – causing a denial of service condition.”
It builds on the flaw behind “Rapid Reset,” Nahum said, “with a neat twist that slips past the common mitigation.”
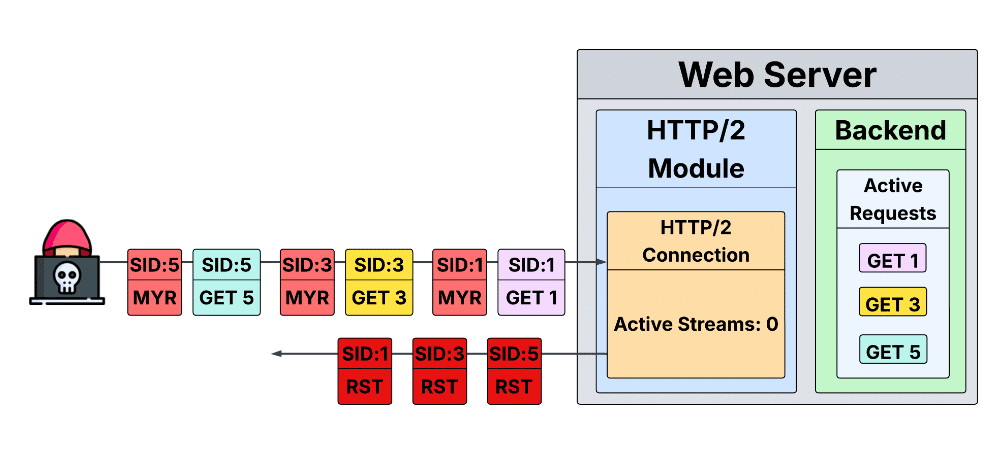
2023’s Rapid Reset took advantage of HTTP/2’s request cancellation feature by opening streams and immediately canceling them using RST_STREAM so they didn’t count toward the MAX_CONCURRENT_STREAMS limit, which by default limits the number of active streams a client can have to 100.
“The mitigation to Rapid Reset that was used by almost all affected implementations was very straightforward – limit the number of streams a client can cancel,” Nahum said.
The researchers found a way around that limit by essentially making the server cancel the request instead of the client, an exploit they’ve dubbed “MadeYouReset.”
“By crafting certain invalid control frames or violating protocol sequencing at just the right moment, we can make the server send RST_STREAM for a stream that already carried a valid request,” Nahum wrote.
The researchers found six such primitives – which exploit WINDOW_UPDATE, PRIORITY, HEADERS and DATA frames – that were covered in a separate technical post.
Vendors Respond to MadeYouReset HTTP/2 Vulnerability
Cloudflare and Akamai said their implementations of HTTP/2 are not vulnerable to CVE-2025-8671, which is classified as an Improper Resource Shutdown or Release vulnerability (CWE-404).
The Carnegie Mellon CERT Coordination Center listed a dozen vendors and projects that were affected by the flaw, some with differing CVEs, CWEs and severity ratings. Most of the affected vendors and projects appear to have issued fixes or mitigations, among them Apache Tomcat, F5, Fastly, h2o, Netty and IBM WebSphere Application Server Liberty.
News of the MadeYouReset flaw also comes as PortSwigger released research detailing major security flaws in HTTP/1.1.
Source: Read More