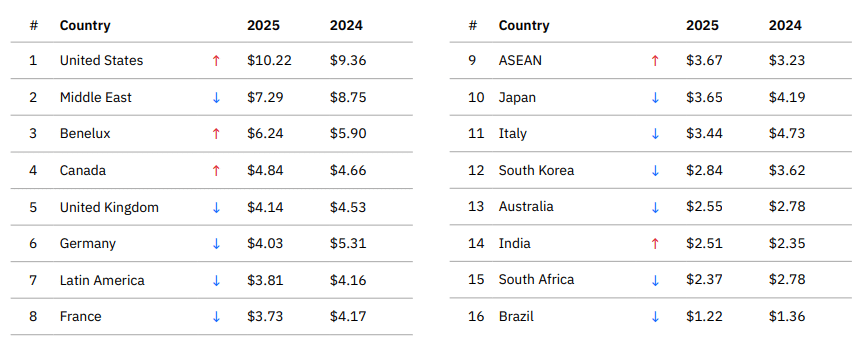Data breaches in the U.S. are getting more costly even as they’re getting cheaper in the rest of the world.
That was one of the conclusions in the new IBM-Ponemon Institute 2025 Cost of a Data Breach report, which also found that AI is playing a significant role in cybersecurity, both as an attack vector and as a defensive measure.
While AI is becoming a significant attack target, AI-powered cybersecurity defenses have significantly cut data breach costs, the report found.
Global Average Data Breach Cost Falls but AI Becomes a Target
While the global average cost of a data breach fell 9% from the 2024 report to $4.44 million – the first decline in five years – the U.S. saw a 9% increase to $10.22 million, an all-time high for any global region. The U.S. increase was largely due to higher regulatory penalties and rising detection costs, the report said.
The global decline was fueled by faster breach containment driven by AI-powered defenses, the report said. At the same time, 16% of breaches involved some use of AI by attackers, often in phishing and deepfake attacks.
AI itself is becoming a significant vulnerability, IBM and Ponemon found. “What we’ve found is concerning: organizations are skipping over security and governance for AI in favor of do-it-now AI adoption,” the report said. “Those ungoverned systems are more likely to be breached—and more costly when they are.”
As a result, 97% of AI-related security breaches involved AI systems that lacked proper access controls. Most breached organizations also have no governance policies in place to manage AI or prevent shadow AI, the report said.
In all, 13% of organizations reported breaches that involved their AI models or applications. The most common security incidents occurred in the AI supply chain, through compromised apps, APIs or plug-ins. The incidents led to a broader data compromise in 60% of cases, and operational disruption in 31% of incidents.
“The findings suggest AI is emerging as a high-value target,” the report said.
Another 20% said they suffered a breach due to security incidents involving shadow AI. Organizations with high levels of shadow AI faced data breach costs that were $670,000 higher than those that had low levels of shadow AI or none. Those incidents also resulted in high rates of personal identifiable information (65%) and intellectual property (40%) data being compromised.
“And that data was most often stored across multiple environments, revealing just one unmonitored AI system can lead to widespread exposure,” the report said. “The swift rise of shadow AI has displaced security skills shortages as one of the top three costly breach factors tracked by this report.”
Even among organizations that have AI governance polices, only a third perform regular audits for unsanctioned AI. “It shows AI remains largely unchecked as adoption outpaces both security and governance,” IBM and Ponemon said.
AI Security Defenses Cut Data Breach Costs
One bright spot in the report is that security teams using AI and automation shortened their breach times by 80 days and lowered their average breach costs by $1.9 million over organizations that don’t use those solutions.
“Nearly a third of organizations said they used these tools extensively across the security lifecycle—in prevention, detection, investigation and response,” the report said. “However, that figure is up only slightly from the previous year, suggesting AI adoption may have stalled. It also shows the majority are still not using AI and automation and, therefore, aren’t seeing the cost benefits.”
Time to identify and contain a breach fell to 241 days, a nine-year low and continuing a downtrend that began after a 287-day peak in 2021.
Malicious insider attacks were the most costly breaches, at $4.92 million, followed by third-party vendor and supply chain attacks at $4.91 million. Other expensive attack vectors included vulnerability exploitation and phishing, which was the most frequent type of attack vector, followed by supply chain compromises (image below).

Healthcare breaches were the most costly, followed by those affecting financial organizations (chart below).

More ransomware victims refused to pay a ransom – 63%, up from 59% in the 2024 report – and law enforcement involvement declined significantly, from 52% to 40% of incidents. The average cost of an extortion or ransomware incident remained high at $5.08 million.
Breaches identified by internal security teams cost less than those first disclosed by third parties or attackers ($4.18 million vs. $5.08 million for attacker-disclosed breaches), as security teams are able to respond faster when they detect attacks first.
The report examined 600 organizations impacted by data breaches between March 2024 and February 2025. Ponemon researchers interviewed 3,470 security and C-suite business leaders with firsthand knowledge of the data breach incidents.
Source: Read More