Cyble threat intelligence researchers identified a phishing campaign aimed at Hungarian government targets that further investigation revealed was connected to wider global attack campaigns targeting the banking and logistics sectors.
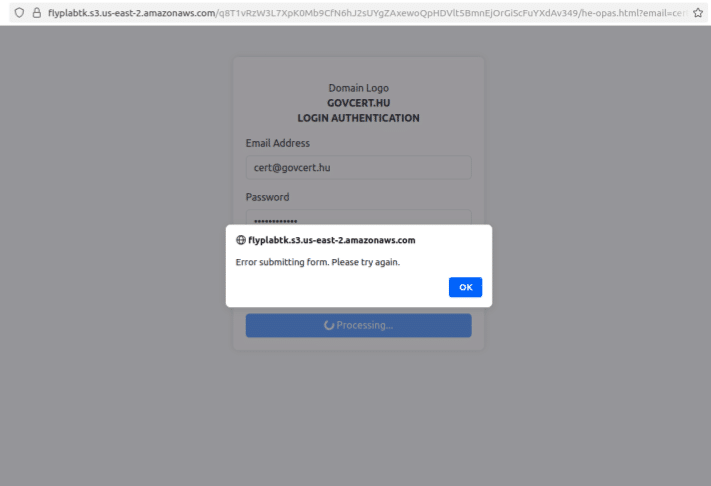
The initial phishing link discovered by the researchers led to a fake login page for HunCERT, Hungary’s Computer Emergency Response Team, Cyble said in a blog post today. The link prefilled the username field with the victim’s email address to increase the chances that the user would submit their credentials.
The phishing links were built using the LogoKit phishing kit, Cyble determined. The phishing pages were hosted on Amazon S3 (AWS) “to stay under the radar and increase credibility among potential victims,” Cyble said. The pages also integrated Cloudflare Turnstile to further the sense of legitimacy.
Those features may have helped the domain harvesting the credentials from being discovered, because the researchers found zero detections on VirusTotal during their work.
LogoKit Phishing Kit Behind Multiple Attack Campaigns
Cyble Research and Intelligence Labs (CRIL) researchers said the phishing URLs used in the campaign used a legitimate HunCERT email address prefilled in the username field.
Cyble included two phishing URLs used in the campaign:
- flyplabtk[.]s3.us-east-2.amazonaws.com/q8T1vRzW3L7XpK0Mb9CfN6hJ2sUYgZAxewoQpHDVlt5BmnEjOrGiScFuYXdAv349/he-opas.html?email=cert@govcert.hu
- flyplabtk[.]s3.us-east-2.amazonaws.com/q8T1vRzW3L7XpK0Mb9CfN6hJ2sUYgZAxewoQpHDVlt5BmnEjOrGiScFuYXdAv349/he-opas.html?email=csirt@nki.gov.hu
The phishing page was designed “to closely resemble a legitimate login portal,” Cyble said, and the Cloudflare Turnstile verification “may deceive users into believing the page is secure” (image below).

A fake error message then tells victims, “Error Submitting form. Please try again.”
The phishing site uses the Clearbit Logo API to fetch the logo from the domain of the targeted organizations, Cyble said, and the Google S2 Favicon retrieves the Favicon icon by extracting the domain from the email address in the URL.
The widely used LogoKit phishing kit leverages “URLs embedded with the victim’s email address, identical layouts, and real-time logo fetching from services like Clearbit and Google’s favicon API,” the researchers said.
“LogoKit remains actively used in phishing campaigns because of its simplicity and automation,” Cyble said. “By automatically retrieving branding icons based on the URL’s domain, threat actors avoid the need to manually locate and update icons or logos within the phishing kit, making the process more scalable, convincing, and efficient.”
Victim credentials are sent to mettcoint[.]com/js/error-200.php. The researchers found an open directory path in mettcoint[.]com that contained several php files and attack elements, and one of the directories contained a phishing page impersonating the WeTransfer file-sharing portal.
OSINT intel revealed that the domain mettcoint[.]com has been used in other phishing attacks. Other targets in the ongoing phishing campaign have included Kina Bank in Papua New Guinea, the Catholic Church in the United States, and logistics companies in Saudi Arabia.
mettcoint[.]com was registered in October 2024 and has been actively leveraged in phishing campaigns since February 2025, Cyble said.
“Notably, the domain currently has zero detections on VirusTotal, allowing it to operate stealthily,” Cyble said. “As of this writing, the domain is still live and functional. Its ongoing availability and undetected status indicate that the phishing campaign is likely still active, with threat actors continuing to target victims on a global scale.”
Protecting Against Phishing Attacks
Cyble said the mettcoint phishing campaigns reveal a major weakness in cybersecurity defenses.
“The human element remains both the strongest and weakest link in cybersecurity, with cautious and responsible use preventing compromises by cyber threats,” the researchers wrote. “Campaigns such as this, however, exploit that element by appearing credible, making them a primary concern for even cyber-savvy employees.”
In addition to a threat intelligence solution that can automatically identify and block threats, Cyble said there are additional cybersecurity best practices that can help stop phishing attacks. Those practices include:
- Being wary of links received via SMS or emails
- Using good antivirus and internet security software on all connected devices
- Educating employees on how to protect themselves from threats like phishing and untrusted URLs
- Using secure email gateways to detect and block phishing emails with malicious links or attachments
- Using multi-factor authentication (MFA) to limit exploitation of stolen credentials
- Monitoring for unusual login behavior or access from suspicious IP addresses
- Keeping devices, operating systems, and applications updated.
Source: Read More