At the absolute basic level, banks take money in and also send money out. Sort of like saying NASA launches spaceships and then bring them back. You know it’s more complicated than the elementary statement, but you know if you had to learn the more advanced functions of banks and NASA, it would likely be much easier to learn how to receive/send money than say landing astronauts on the surface of the moon.
Despite moving money from inside a bank to someplace else since at least 15th Century Italy, banks still make mistakes sending money outside the bank. When they make a mistake, there are penalties. In the United States, banks, regulators and quasi-regulators such as ACH have set out a series of monetary penalties, called compensation, for mistakes sending money outside the bank. The penalties depend on which party (sending or receiving financial institution) caused the error; the amount of the error; how long the error persisted; and interest rates.
In an effort to show how payment errors can be reduced, in this blog we’re going to list out the five biggest categories of errors including an example of each type and point out where/when Artificial Intelligence (“AI”) can be used to reduce payment errors and the corresponding compensation on those errors.
Estimated bank payment errors, also known as improper payments, are a significant concern, with the Government Accountability Office (“GAO”) of the federal government reporting an estimated $247 billion in errors in fiscal year 2022. The government also estimates that 50% of payment errors are attributable to human errors. This emphasizes the value of automated mitigation and both human and software monitoring systems.
Error Types
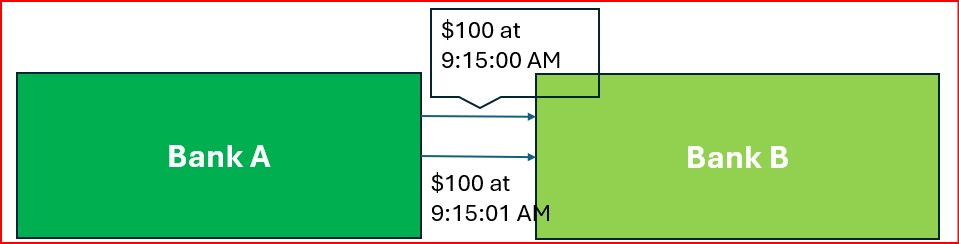
I. Duplicate Payments
Duplicate payments from banks will often be due to system glitches, such as shown below where a payment was processed twice, or at times the error is caused by bad human input such as a middle office processing a trade incorrectly, sending payment, and later processing the trade correctly but sending payment out a second time incorrectly.
Software, whether straight through processing or AI software to detect potential double payments is now being established by banks focusing detection on duplicate matching criteria with key payment attributes with transaction identifiers, often an alphanumeric code assigned to each transaction, acting as sort of a digital fingerprint. They enable banks, merchants, and customers to easily identify, track, and reference specific transactions for various purposes, including record-keeping, dispute resolution, and fraud detection.
II. Incorrect Payment Amount
A landmark case of an incorrect payment amount occurred in April 2024 when a staff member at a bank in New York City copied the account number of one system into the field intended for the dollar figure of a second system.
The error was caught the next business day and had to be reported to regulators as a “Near-Miss”. The “copy and paste error” as it has become known was manual and unintentional, but still caused bank management embarrassment, and showed how despite billions spent on information technology at financial institutions at times controls haven’t improved much from the days of 8-column ledger cards.
Straight through processing, which would have avoided a staff member from copying and pasting bank accounts and dollar amounts from one system to another could have avoided the situation altogether. The old four-eyed check, the bank in question had that in place and it was still missed. If you’re a bank executive looking to reduce errors, would you look to instill software that processes payments automatically or would you look to start a six-eyed check?
III. Incorrect Currency
Ever see a structured note that you buy in one currency, pays interest in a second currency, and depending on what the stock market indexes return over the period between offering date and maturity date pays the final principal in either the original or depending on the calculation outlined in the Offering Circular, a third, or even a fourth currency?
If you’re a bank executive looking to improve the payment experience and reduce errors, are you more likely to trust the third worker to take over the account since inception who’s been with the bank since they graduated months ago, or software that can read the final Offering Circular, research and calculate the different payment (interest rate, stock market index returns, foreign currency exchange rates, etc.) and execute the payment? Yeah, me too.
IV. Incorrect Payee and/or Payor

Software, particularly AI software that has been coded to look for anomaly detection using individual payments, aggregate payments, frequency, payment trends and debtor-credit payment histories is helping reduce cases where the wrong payee is paid or the correct payee is paid, but with money from the wrong payor account.
V. Potential Fraud
AI software enhances fraud protection and detection by leveraging machine learning to analyze vast datasets, identify patterns, and adept itself to evolving fraud tactics. The software improves accuracy, reduces false positives, and enables real-time monitoring for immediate intervention. Compared to four-eyed checks and older payment processing systems, AI-powered fraud detection software platforms offer the advantages of:
- monitoring transactions and activities in real-time, flagging suspicious events as they occur.
- allowing for immediate intervention, such as blocking a fraudulent transaction or freezing an account, preventing further losses, embarrassment (aka “Headline Risk”), and reporting to federal regulators of “near-misses”.
- Traditional systems often rely on batch processing, which can result in delays and allow fraudulent activities to continue for a longer period.
Ready to explore your firm’s payments strategy?
Our financial services experts continuously monitor the regulatory landscape and deliver pragmatic, scalable solutions that meet the mandate and more. Reach out to Perficient’s Financial Services Managing Director David Weisel to discover why we’ve been trusted by 18 of the top 20 banks, 16 of the 20 largest wealth and asset management firms, and are regularly recognized by leading analyst firms.
It’s that component, the Subject Matter Expert (“SME”) that is the most important component of the mathematical expression in the title. Software helps. AI software helps a lot. But it’s the SME installing and reconfiguring processes and controls along with the AI software that helps the most.
Source: Read MoreÂ