One bright spot in Sophos’ annual State of Ransomware report released this week is that organizations have gotten better at stopping ransomware attacks before attackers are able to encrypt data.
But otherwise the report shows that defensive and preventive preparation continues to lag, if not backslide in some cases.
Ransomware Response Improves as Backup Lags
The report, based on a survey of 3,400 IT and cybersecurity leaders in 17 countries whose organizations were hit by ransomware attacks in the last year, found that 44% of organizations were able to stop the attack before data was encrypted. That’s the highest rate in the survey’s six-year-history (image below).

Data was encrypted in half the cases, the lowest rate in the survey’s history, while in 6% of cases organizations faced extortion demands even when data wasn’t encrypted.
The report also noted that:
- 28% of organizations that had data encrypted also experienced data exfiltration.
- 97% that had data encrypted were able to recover it.
- The use of backups to restore encrypted data is at the lowest rate in six years, used in just 54% of incidents.
- 49% of victims paid the ransom to get their data back, the second highest ransom payment rate in six years.
Looking at recovery from backups vs. the percentage of ransom payments, the trend begins to appear worrisome, as successful backup recovery has declined significantly, from 73% in 2022 to 54% this year, while the percentage of ransom payments has generally been trending higher throughout the report’s history (chart below).

The average ransom payment fell from $2 million in 2024 to $1 million in 2025, largely because of a sizeable drop in ransom payments of $5 million or more. On average, ransom payments were 85% of the amount demanded; 29% said their payment matched the demand, 53% paid less and 18% paid more.
Excluding ransoms, the average cost to recover from a ransomware attack dropped from $2.73 million in 2024 to $1.53 million. More than half of organizations – 53% – fully recovered in a week, up from 35% in 2024.
Also read: SafePay, DevMan Emerge as Major Ransomware Threats
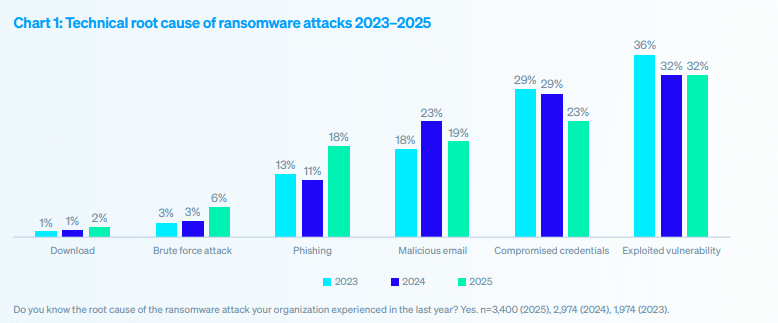
The Root Causes of Ransomware Attacks
For the third straight year, ransomware victims said vulnerabilities were the most common technical root cause of an attack, exploited by attackers in 32% of incidents.
Compromised credentials were the second most common attack vector even as those attacks fell from 29% in 2024 to 23% in 2025. 19% of victims reporting malicious email as the root cause and 18% citing phishing.
A lack of expertise was a factor in 40.2% of attacks, followed by unknown security gaps at 40.1%. Lack of people and capacity was cited in 39.4% of attacks.
Overall, the report suggests that organizations still have much progress to make on essential ransomware protections such as vulnerability management, segmentation and zero trust, ransomware-resistant backups, and infrastructure and endpoint hardening and monitoring.
Source: Read More