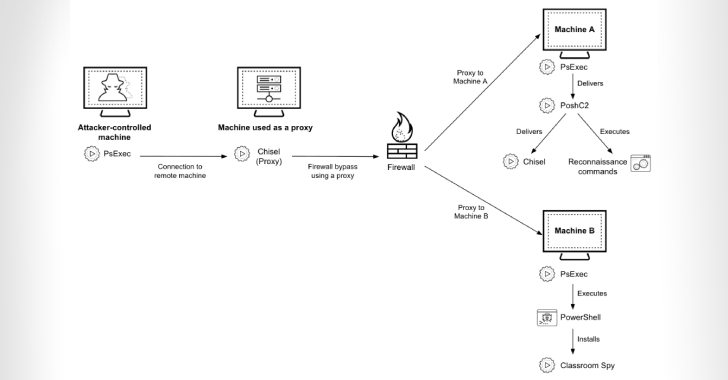
Cybersecurity researchers are calling attention to a series of cyber attacks targeting financial organizations across Africa since at least July 2023 using a mix of open-source and publicly available tools to maintain access.
Palo Alto Networks Unit 42 is tracking the activity under the moniker CL-CRI-1014, where “CL” refers to “cluster” and “CRI” stands for “criminal motivation.”
It’s suspected
Source: Read More