In our some previous articles we have talked about data-privacy and VPN. If we are using Kali Linux, and we need to use a VPN for it then our this easy and short tutorial will help a lot.
Proton VPN is a Swiss based (Switzerland which has some of the world’s strongest privacy laws) Free and reliable Virtual Private Network which will give us security, privacy and freedom from Internet censorship, allowing us to access any website or content. In our this detailed guide we are going to learn how we can set the Proton VPN GUI (Graphical User Interface) application on our Kali Linux system.
Key Features of Proton VPN
- No activity logs
- Open source
- Strong encryption
- Swiss privacy
- Kill Switch and Always-on VPN
- Tor over VPN
- DNS leak protection
- VPN Accelerator
- NetShield Ad-blocker
- Worldwide streaming
There was a premium feature of this VPN ($5 USD/month) with more servers and connection with a higher speed. We don’t promote this, so we suggest to go with the basic free plan. Let’s install this mighty VPN on our system.
Installing Proton VPN on Kali Linux
First of all we need to download Proton VPN’s DEB package installs the Proton VPN repository on our system. We can click here to download the DEB package of Proton VPN.
It will be downloaded on our ~/Downloads directory by default. So we need to run following command on our terminal window:
sudo apt-get install ~/Downloads/protonvpn-stable-release_1.0.1-1_all.debThe output of the above screenshot shows in the following screenshot:
This will take some time to finish, then we need to update our system by running following command:
sudo apt-get updateAfter the updating is complete, we need to install ProtonVPN by running following command:
sudo apt-get install protonvpnThe above command will install ProtonVPN as we can see in the following screenshot:
The installation process will not take much time. After the process is complete ProtonVPN will be installed on our Kali Linux.
Using Proton VPN on Kali Linux
After Installing Proton VPN we can see ProtonVPN on our Application Menu.
Now we need to open it, we will see ProtonVPN client as we can see in the following screenshot:
Here we need click on “Create Account” to create an ProtonVPN account. We just need to create a username and a password and provide our e-mail address and verify it.
Pro Tip:- We can use temp-mail services to register on Proton VPN due to maintain our privacy.
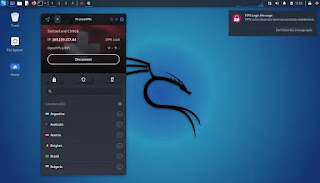
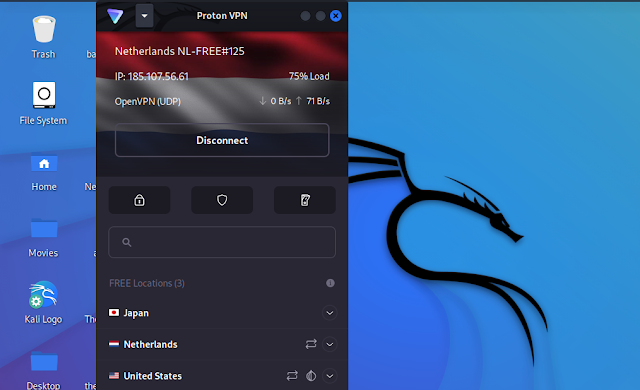
After creating an account we can login in the ProtonVPN client application on our system, then connect it and use it as simple as shown in the following screenshot:
Now it is very easy to use. We don’t need to remember commands or configuration files like other VPNs for Kali Linux. This is quite simple like any mobile VPN application.
In this article we learned how we can simply use VPN apps on Kali Linux, Proton VPN on Kali is very simple and easy to use. The above method can be applied for other Debian based Linux distributions like Ubuntu, Linux Mint and Elementary OS etc.
Love our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group and Whatsapp Channel. We are trying to build a community for Linux and Cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Source: Read More