Unsophisticated hackers are increasingly targeting industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems in the energy and transportation sectors, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned in an advisory yesterday.
“Although these activities often include basic and elementary intrusion techniques, the presence of poor cyber hygiene and exposed assets can escalate these threats, leading to significant consequences such as defacement, configuration changes, operational disruptions and, in severe cases, physical damage,” CISA said in the May 6 alert.
CISA – along with the FBI, the Environmental Protection Agency (EPA), and the Department of Energy (DOE) – urged critical infrastructure asset owners and operators to implement guidance for reducing the risk of attacks on ICS/SCADA systems.
Russia-Linked Groups Have Tampered with ICS/SCADA Controls: Cyble
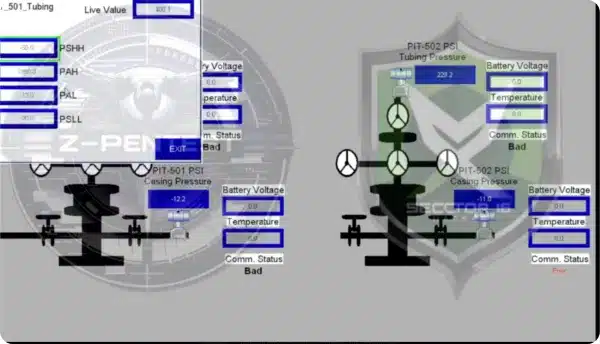
CISA didn’t name the threat actors targeting ICS/SCADA systems, but Cyble has reported on Russia-linked threat groups Z-Pentest, Sector 16, the People’s Cyber Army and other groups hacking into operational technology (OT) control panels in energy and water systems and tampering with settings.
In one case, Z-Pentest claimed to have disrupted a U.S. oil well system, a claim that was unconfirmed. The groups often post screen recordings of members tampering with operational control panel settings.
While it’s not clear how much ICS expertise the groups have or how much damage they’re capable of doing, Cyble said in one report that Z-Pentest “should be taken seriously, as the group has demonstrated an apparent ability to penetrate these environments and access – and tinker with – operational control panels.”
The hacktivist groups often cite support for Ukraine as the reason for their cyberattacks in the U.S. and other countries, which have included Canada, Australia, France, South Korea, Taiwan, Italy, Romania, Germany, and Poland.
In addition to Russia-linked groups, China-linked threat actors are believed to have compromised U.S. critical infrastructure, potentially in preparation for an invasion of Taiwan.
Critical Infrastructure Cybersecurity Guidance
CISA and the other federal agencies issued guidance for critical infrastructure organizations “to improve their cybersecurity posture against cyber threat activities specifically and intentionally targeting internet connected OT and ICS.”
The guidance includes:
Removing OT connections to the public internet: “OT devices lack authentication and authorization methods that are resistant to modern threats and are quickly found by searching for open ports on public IP ranges with search engine tools to target victims with OT components,” the guidance says.
Changing default passwords immediately and using strong, unique passwords: “Recent analysis of this cyber activity indicates that targeted systems use default or easily guessable (using open source tools) passwords. Changing default passwords is especially important for public-facing internet devices that have the capability to control OT systems or processes.”
Securing remote access to OT networks: “If remote access is essential, upgrade to a private IP network connection to remove these OT assets from the public internet and use virtual private network (VPN) functionality with a strong password and phishing-resistant multifactor authentication (MFA) for user remote access.”
Segmenting IT and OT networks: “Segmenting critical systems and introducing a demilitarized zone for passing control data to enterprise logistics reduces the potential impact of cyber threats and reduces the risk of disruptions to essential OT operations.”
Practicing and maintaining the ability to operate OT systems manually: “The capability for organizations to revert to manual controls to quickly restore operations is vital in the immediate aftermath of an incident. Business continuity and disaster recovery plans, fail-safe mechanisms, islanding capabilities, software backups, and standby systems should all be routinely tested to ensure safe manual operations in the event of an incident.”
The agencies also recommended regular communication with managed service providers, system integrators, and system manufacturers for system-specific configuration guidance for securing OT environments.
Source: Read More