So, we all have searched for hacking tools that can magically find vulnerabilities in a website or server. Almost every beginner in cybersecurity wants to find a tool that automates the entire process, so they can sit back and watch the results. After finishing this tutorial, we will have a clear idea of AutoRecon, an amazing automated reconnaissance tool. Not just for bug bounty hunters, this tool is useful for penetration testers, ethical hackers, and even those who are just curious about how reconnaissance works. This tool helped a lot everyone in OSCP and in the HackTheBox.
The Truth About Automated Recon
First of all, let’s be clear—there’s no “one-click hacking tool” that will instantly find and exploit vulnerabilities like in movies. But when we search for automated recon tools, we see a flood of scripts and frameworks claiming to do everything. If we believe in those “magic hack” tools, congratulations—we’ve unlocked a higher level of foolishness.
AutoRecon is not a hacking tool that will instantly pop a shell on a target. It is a powerful reconnaissance tool that helps ethical hackers gather information efficiently. If we know how to use it correctly, it will make our job easier, but it won’t do everything for us. In this detailed article we are going to install AutoRecon on our Kali Linux system and we will se some use of it.
Installing AutoRecon on Kali Linux
Installing AutoRecon on Kali Linux is very easy, cause it comes with Kali Linux repository. So we just need to apply following command for a hassle-free installation:
sudo apt install autorecon -y
The following screenshot shows the output of applied command.
In our case it prompt for some libraries to restart. Here we just need to press the TAB button and Enter Key (If doesn’t work then re-logging or restarting the system is an option).
Now we are ready to use the AutoRecon on our Kali Linux system.
Using AutoRecon on Kali Linux
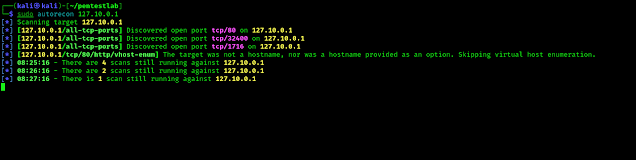
Now the last thing to do. We just need to run AutoRecon against a target. For just an example we are running it on to our localhost server. Here our target address is 1227.10.0.1 (on real life based target this thing could be like something.com). We just need to apply simple command as following:
sudo autorecon 127.10.0.1It will start the process automatically as we can see in the following screenshot:
After giving it a decent amount of time it completes it’s scanning process. Then we have to find the search results. Autorecon automatically creates a directory called “results” where in which directory it was running. So after the scanning process is done we need to go to the results directory by command line (or by using mouse clicks on file manager). in the results directory we can find another directory (named after our target’s URL) where all the scan results are stored. On the following screenshot we just showed the CVE’s we found on our target, but there are lot of good stuffs are out there. We are not going to spoonfeed everything. Try them out. We are just showing that we found some vulnerabilities on our target as we can see in the following screenshot:
This is how we can easily found various information even vulnerabilities on our targeted website using AutoRecon on our Kali Linux system. AutoRecon is very useful tool for bug bounty hunters, cybersecurity researchers and OSCP students.
Enjoy our articles? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group & Whatsapp Channel. We are striving to build a community for Linux and cybersecurity. For anything we always happy to help everyone on the comment section and on Telegram Group. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Source: Read More