Cyble threat intelligence researchers have uncovered a GitHub repository masquerading as a hiring coding challenge that tricks developers into downloading a backdoor to steal sensitive data.
The campaign uses a number of unusual techniques, such as using a social media profile for command and control (C&C) activities instead of C&C servers.
There is evidence that the campaign may be expanding beyond a fake hiring challenge for developers, as Cyble Research and Intelligence Labs (CRIL) researchers also found invoice-themed lures.
Fake Hiring Challenge Targets Polish Developers
The Cyble researchers said in a blog post that the campaign appears to target Polish-speaking developers, and the malware uses geofencing to restrict execution. The researchers speculated that the campaign is delivered via job platforms like LinkedIn or regional developer forums.
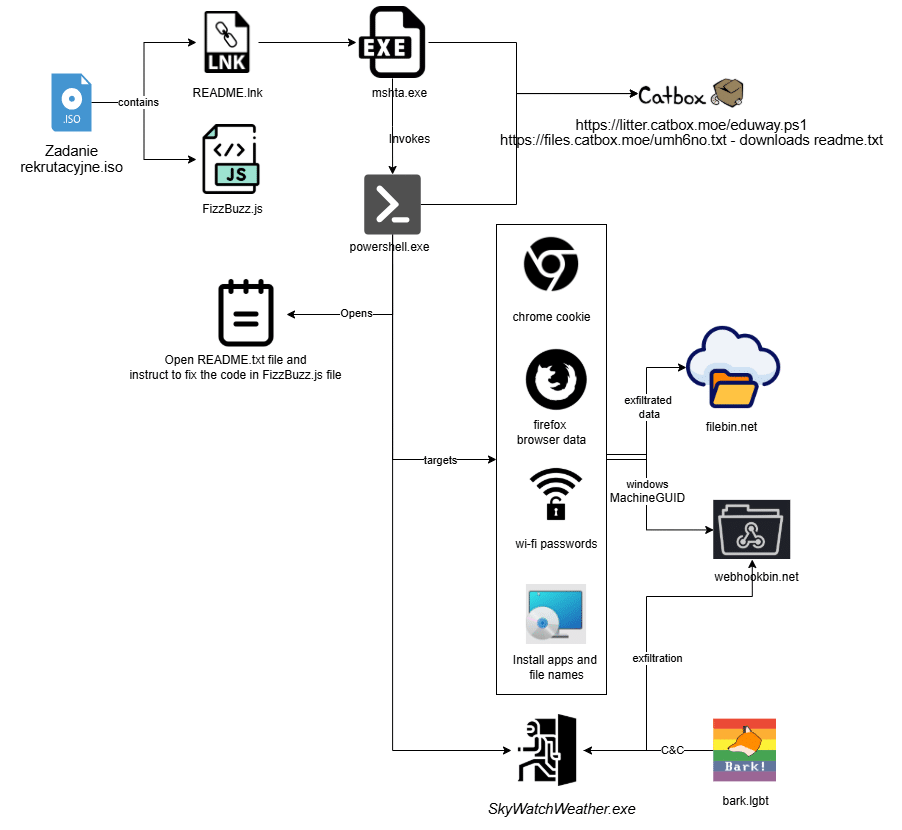
The fake recruitment test, named “FizzBuzz,“ is used to trick victims into downloading an ISO file containing a JavaScript exercise and a malicious LNK shortcut. When executed, the LNK file (“README.lnk”) runs a PowerShell script that installs a stealthy backdoor dubbed “FogDoor” by the researchers.
“This backdoor is designed for persistence, data theft, and remote command execution while avoiding detection,” Cyble wrote.
Instead of using C&C servers, FogDoor communicates with a social media platform via a Dead Drop Resolver (DDR) technique, retrieving attack commands from a social media profile, the researchers said.
The malware uses geofencing to restrict execution to Polish victims. Once active, “it systematically steals browser cookies, Wi-Fi credentials, and system data, staging them for exfiltration before deleting traces,” Cyble said.
The malware uses remote debugging to steal Chrome cookies and can operate in background mode, while Firefox credentials are taken from profile directories.
PowerShell Script Establishes Persistence
The PowerShell script also opens a “README.txt” file “to mislead users into believing they are interacting with a harmless file,” Cyble said.
That document contains instructions for a code bug fix task, “making it appear harmless while ensuring the PowerShell script executes only once on the victim’s machine to carry out malicious activities.”
The PowerShell script also downloads an executable file and saves it as “SkyWatchWeather.exe” in the “C:UsersPublicDownloads” folder and creates a scheduled task named “Weather Widget,” which executes the downloaded file using mshta.exe and VBScript and is set to run every two minutes indefinitely.
SkyWatchWeather.exe acts as a backdoor by using a social media platform (bark.lgbt) and a temporary webhook service (webhookbin.net) as its C&C infrastructure. After verifying location, the malware attempts to establish a connection with “bark.lgbt/api” to await further commands, which are embedded within the profile information of a social media platform. That setup also makes detection and takedown efforts more challenging, Cyble said.
Stopping Hiring Scams and Cyberattacks
The researchers had a number of recommendations for protecting against FizzBuzz, FogDoor and similar attacks, such as:
- Cross-checking job offers and coding challenges from unverified sources
- Refraining from downloading and running files from unknown repositories, particularly ISO images and script files
- Restricting the execution of PowerShell, JavaScript and other scripting languages unless explicitly required, and using application whitelisting
- Monitoring outbound connections to uncommon domains or file-sharing services
- Protecting browser-stored credentials with multi-factor authentication (MFA) and password managers.
The full Cyble blog contains deeper analysis of the campaign and includes Yara and Sigma detection rules, indicators of compromise (IoCs) and MITRE ATT&CK techniques.
Source: Read More