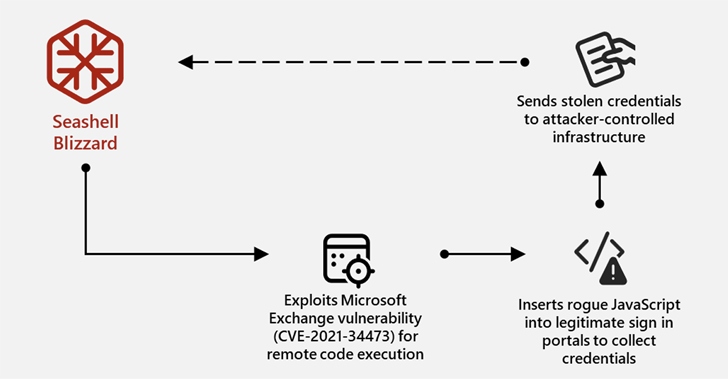
A subgroup within the infamous Russian state-sponsored hacking group known as Sandworm has been attributed to a multi-year initial access operation dubbed BadPilot that stretched across the globe.
“This subgroup has conducted globally diverse compromises of Internet-facing infrastructure to enable Seashell Blizzard to persist on high-value targets and support tailored network operations,” the
Source: Read More