

Ad hoc networks are decentralized, self-configuring networks where nodes communicate without fixed infrastructure. They are commonly used in military, disaster recovery, and IoT applications. Each node acts as both a host and a router, dynamically forwarding data.
Flooding attacks in ad hoc networks occur when a malicious node excessively transmits fake route requests or data packets, overwhelming the network. This leads to resource exhaustion, increased latency, and potential network failure.
Recent works on flooding attack mitigation in ad hoc networks focus on trust-based routing, machine learning classification, and adaptive intrusion detection. Techniques like SVM, neural networks, and optimization algorithms improve attack detection, reliability, and network performance. Hybrid models further enhance accuracy and reduce false alarms. Despite notable progress in mitigating such attacks in MANETs, current methods struggle to balance detection accuracy, maintain energy efficiency, and adapt to rapidly changing network conditions.
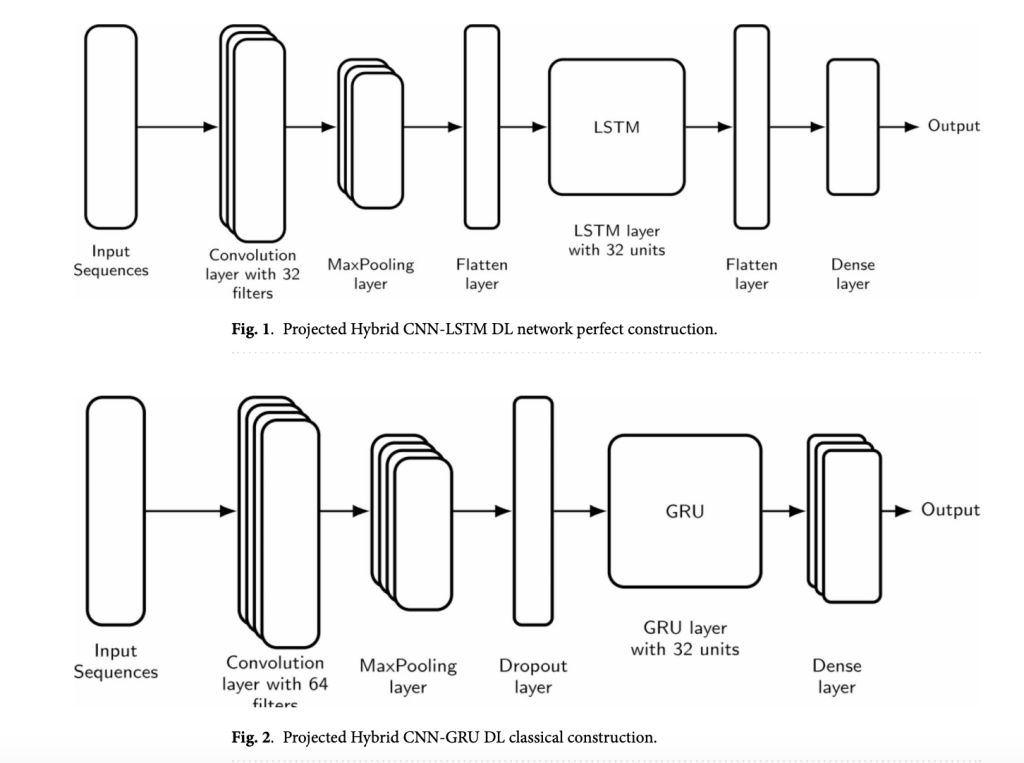
As a response to these challenges, a new paper was recently published proposing an energy-efficient hybrid routing protocol to mitigate flooding attacks in MANETs using a CNN-LSTM/GRU model for classification. The hybrid approach integrates machine learning with the routing protocol to optimize energy efficiency while preventing attacks. The model classifies nodes as trusted or untrusted based on their packet transmission behavior, blacklisting those that exceed predefined thresholds. Training involves extracting features from both benign and malicious nodes, with classification relying on learned patterns.
To enhance accuracy, the model applies CNN for feature extraction, followed by LSTM or GRU for sequence learning, optimizing decision-making in real-time. The protocol eliminates malicious nodes upon detecting RREQ flooding attacks, ensuring energy conservation. MATLAB is used to create a training dataset and implement an Euclidean distance-based classification. Trust estimation uses link expiration time (LET) and residual energy (RE), with nodes requiring a minimum trust value of 0.5 to participate in routing. Finally, the ML-based AODV protocol selects nodes with the highest trust values to optimize packet delivery and minimize rerouting.
To evaluate the proposed approach, the research team conducted simulations in MATLAB R2023a to assess the performance of a hybrid deep learning model for flooding attack detection in MANETs. The simulation environment accurately modeled the physical layer of MANETs to ensure realistic evaluation conditions. Key performance metrics were analyzed, including packet delivery ratio, throughput, routing overhead, stability time of cluster heads, and attack detection time.
The results demonstrated that the proposed model outperformed existing DBN, CNN, and LSTM approaches. It achieved a higher packet delivery ratio (96.10% for 60 nodes), improved throughput (263 kbps for 100 nodes), and lower routing overhead. Moreover, it exhibited faster attack detection times, outperforming LSTM, CNN, and DBN. Classification performance metrics further confirmed its superiority, with 95% accuracy, 90% specificity, and 100% sensitivity. These findings validate the model’s effectiveness in enhancing MANET security.
The proposed hybrid deep learning model shows promise in mitigating flooding attacks but has limitations. Its computational complexity increases with network size, limiting real-time use in large networks, and it requires substantial memory and processing power. Additionally, relying on MATLAB simulations may not fully reflect real-world MANET dynamics. Regular updates and retraining are also needed to adapt to evolving attack strategies.
In conclusion, while the hybrid models (CNN-LSTM and CNN-GRU) outperform baseline approaches, challenges like computational overhead and evolving attacks remain.
Check out the Paper. All credit for this research goes to the researchers of this project. Also, don’t forget to follow us on Twitter and join our Telegram Channel and LinkedIn Group. Don’t Forget to join our 75k+ ML SubReddit.
The post Enhancing Mobile Ad Hoc Network Security: A Hybrid Deep Learning Model for Flooding Attack Detection appeared first on MarkTechPost.
Source: Read MoreÂ


 Recommended Open-Source AI Platform: ‘IntellAgent is a An Open-Source Multi-Agent Framework to Evaluate Complex Conversational AI System’ (Promoted)
Recommended Open-Source AI Platform: ‘IntellAgent is a An Open-Source Multi-Agent Framework to Evaluate Complex Conversational AI System’ (Promoted)