Please help me learn how to identify problems in Appium mobile automation: I don’t know where to look to identify the error.
I built a test app with android-sdk on my physical mobile phone.
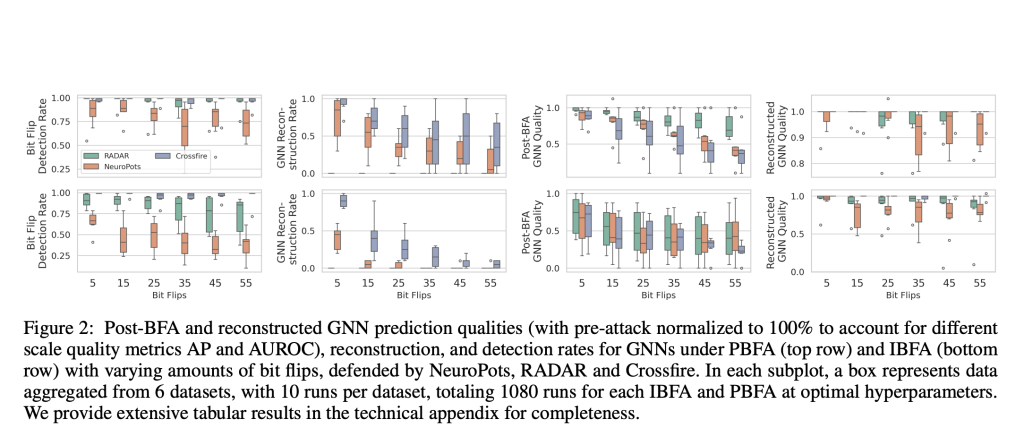
I took a little Appium test in java just to launch the test app on a connected physical Android device – a Huawei P30Pro.
this test is from a good tutorial with no errors in eclipse. It sure should be fine, the pom.xml too.
Appium server v1.22.3 is running in one instance
in Eclipse, I press the test Button Run as Java Application
the server window starts writing many lines like it’s working
Problem is:
1.) The Server writes many lines when working (is this the Server log (What/where is a stack trace?))
But suddenly comes the last line:
[HTTP] <– POST /wd/hub/session 500 4111 ms – 637
[HTTP]
1.b) at this moment the Eclipse console writes:
Server-side error occurred while processing Appium-server
Driver info: driver.version: AppiumDriver
org.openqa.selenium.SessionNotCreatedException: Unable to create a new remote session. Please check the server log for more details.
Original error: An unknown server-side error occurred while processing the command. Original error: ‘app’ option is required for reinstall
… 12 more
2.) The Test-App is not launching at mobile device
But I have Android-Notification from Appium Settings ‘Keep this service running, so Appium for Android can work with system APIs’
My question is:
How can I find why <– POST /wd/hub/session has State=500
And why does this error come so late; why not at beginning
The server is running
The server is running
[Appium] Welcome to Appium v1.22.3
[Appium] Non-default server args:
[Appium] relaxedSecurityEnabled: true
[Appium] allowInsecure: {
[Appium] }
[Appium] denyInsecure: {
[Appium] }
[Appium] Appium REST http interface listener started on 0.0.0.0:4723
[HTTP] –> POST /wd/hub/session
[HTTP] {“desiredCapabilities”:{“appActivity”:”com.example.yeshasprabhakar.todo.MainActivity”,”appPackage”:”com.example.yeshasprabhakar.todo1.0″,”platformName”:”Android”,”udid”:”22X0220428007340″,”platformVersion”:”10.0″},”capabilities”:{“firstMatch”:[{“appium:appActivity”:”com.example.yeshasprabhakar.todo.MainActivity”,”appium:appPackage”:”com.example.yeshasprabhakar.todo1.0″,”platformName”:”android”,”appium:platformVersion”:”10.0″,”appium:udid”:”22X0220428007340″}]}}
[W3C] Calling AppiumDriver.createSession() with args: [{“appActivity”:”com.example.yeshasprabhakar.todo.MainActivity”,”appPackage”:”com.example.yeshasprabhakar.todo1.0″,”platformName”:”Android”,”udid”:”22X0220428007340″,”platformVersion”:”10.0″},null,{“firstMatch”:[{“appium:appActivity”:”com.example.yeshasprabhakar.todo.MainActivity”,”appium:appPackage”:”com.example.yeshasprabhakar.todo1.0″,”platformName”:”android”,”appium:platformVersion”:”10.0″,”appium:udid”:”22X0220428007340″}]}]
[BaseDriver] Event ‘newSessionRequested’ logged at 1665348795592 (22:53:15 GMT+0200 (Mitteleuropäische Sommerzeit))
[Appium]
[Appium] ======================================================================
[Appium] DEPRECATION WARNING:
[Appium]
[Appium] The ‘automationName’ capability was not provided in the desired
[Appium] capabilities for this Android session
[Appium]
[Appium] Setting ‘automationName=UiAutomator2’ by default and using the
[Appium] UiAutomator2 Driver
[Appium]
[Appium] The next major version of Appium (2.x) will **require** the
[Appium] ‘automationName’ capability to be set for all sessions on all
[Appium] platforms
[Appium]
[Appium] In previous versions (Appium <= 1.13.x), the default was
[Appium] ‘automationName=UiAutomator1’
[Appium]
[Appium] If you wish to use that automation instead of UiAutomator2, please
[Appium] add ‘automationName=UiAutomator1’ to your desired capabilities
[Appium]
[Appium] For more information about drivers, please visit
[Appium] http://appium.io/docs/en/about-appium/intro/ and explore the
[Appium] ‘Drivers’ menu
[Appium]
[Appium] ======================================================================
[Appium]
[Appium] Appium v1.22.3 creating new AndroidUiautomator2Driver (v1.70.1) session
[Appium] Applying relaxed security to ‘AndroidUiautomator2Driver’ as per server command line argument. All insecure features will be enabled unless explicitly disabled by –deny-insecure
[BaseDriver] W3C capabilities and MJSONWP desired capabilities were provided
[BaseDriver] Creating session with W3C capabilities: {
[BaseDriver] “alwaysMatch”: {
[BaseDriver] “platformName”: “android”,
[BaseDriver] “appium:appActivity”: “com.example.yeshasprabhakar.todo.MainActivity”,
[BaseDriver] “appium:appPackage”: “com.example.yeshasprabhakar.todo1.0”,
[BaseDriver] “appium:platformVersion”: “10.0”,
[BaseDriver] “appium:udid”: “22X0220428007340”
[BaseDriver] },
[BaseDriver] “firstMatch”: [
[BaseDriver] {}
[BaseDriver] ]
[BaseDriver] }
[BaseDriver] Session created with session id: cf0a35b0-da66-4fa9-a6c7-b4aca880f564
[UiAutomator2] Starting ‘com.example.yeshasprabhakar.todo1.0’ directly on the device
[ADB] Found 3 ‘build-tools’ folders under ‘C:UserscauseAppDataLocalAndroidSdk’ (newest first):
[ADB] C:/Users/cause/AppData/Local/Android/Sdk/build-tools/33.0.0
[ADB] C:/Users/cause/AppData/Local/Android/Sdk/build-tools/30.0.3
[ADB] C:/Users/cause/AppData/Local/Android/Sdk/build-tools/29.0.3
[ADB] Using ‘adb.exe’ from ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe’
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 start-server’
[AndroidDriver] Retrieving device list
[ADB] Trying to find a connected android device
[ADB] Getting connected devices
[ADB] Connected devices: [{“udid”:”22X0220428007340″,”state”:”device”}]
[AndroidDriver] Using device: 22X0220428007340
[ADB] Using ‘adb.exe’ from ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe’
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 start-server’
[ADB] Setting device id to 22X0220428007340
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell getprop ro.build.version.sdk’
[ADB] Current device property ‘ro.build.version.sdk’: 29
[ADB] Getting device platform version
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell getprop ro.build.version.release’
[ADB] Current device property ‘ro.build.version.release’: 10
[ADB] Device API level: 29
[UiAutomator2] Relaxing hidden api policy
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell ‘settings put global hidden_api_policy_pre_p_apps 1;settings put global hidden_api_policy_p_apps 1;settings put global hidden_api_policy 1”
[AndroidDriver] No app sent in, not parsing package/activity
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 wait-for-device’
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell echo ping’
[AndroidDriver] Pushing settings apk to device…
[ADB] Getting install status for io.appium.settings
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell dumpsys package io.appium.settings’
[ADB] ‘io.appium.settings’ is installed
[ADB] Getting package info for ‘io.appium.settings’
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell dumpsys package io.appium.settings’
[ADB] The version name of the installed ‘io.appium.settings’ is greater or equal to the application version name (‘3.4.0’ >= ‘3.4.0’)
[ADB] There is no need to install/upgrade ‘C:Program FilesAppium Server GUIresourcesappnode_modulesappiumnode_modulesio.appium.settingsapkssettings_apk-debug.apk’
[ADB] Getting IDs of all ‘io.appium.settings’ processes
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell ‘pgrep –help; echo $?”
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell pgrep -f ([[:blank:]]|^)io.appium.settings([[:blank:]]|$)’
[AndroidDriver] io.appium.settings is already running. There is no need to reset its permissions.
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell appops set io.appium.settings android:mock_location allow’
[Logcat] Starting logs capture with command: C:\Users\cause\AppData\Local\Android\Sdk\platform-tools\adb.exe -P 5037 -s 22X0220428007340 logcat -v threadtime
[UiAutomator2] Forwarding UiAutomator2 Server port 6790 to local port 8200
[ADB] Forwarding system: 8200 to device: 6790
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 forward tcp:8200 tcp:6790’
[UiAutomator2] Server package at ‘C:Program FilesAppium Server GUIresourcesappnode_modulesappiumnode_modulesappium-uiautomator2-serverapksappium-uiautomator2-server-v4.27.0.apk’ is not writeable. Will copy it into the temporary location at ‘C:UserscauseAppDataLocalTemp202299-19828-1p2wn9i.yjgq’ as a workaround. Consider making this file writeable manually in order to improve the performance of session startup.
[UiAutomator2] Server package at ‘C:Program FilesAppium Server GUIresourcesappnode_modulesappiumnode_modulesappium-uiautomator2-serverapksappium-uiautomator2-server-debug-androidTest.apk’ is not writeable. Will copy it into the temporary location at ‘C:UserscauseAppDataLocalTemp202299-19828-1p2wn9i.yjgq’ as a workaround. Consider making this file writeable manually in order to improve the performance of session startup.
[ADB] Getting install status for io.appium.uiautomator2.server
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell dumpsys package io.appium.uiautomator2.server’
[ADB] ‘io.appium.uiautomator2.server’ is installed
[ADB] Getting package info for ‘io.appium.uiautomator2.server’
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell dumpsys package io.appium.uiautomator2.server’
[ADB] The version name of the installed ‘io.appium.uiautomator2.server’ is greater or equal to the application version name (‘4.27.0’ >= ‘4.27.0’)
[UiAutomator2] io.appium.uiautomator2.server installation state: sameVersionInstalled
[ADB] Checking app cert for C:UserscauseAppDataLocalTemp202299-19828-1p2wn9i.yjgqappium-uiautomator2-server-v4.27.0.apk
[ADB] Using ‘apksigner.jar’ from ‘C:UserscauseAppDataLocalAndroidSdkbuild-tools33.0.0libapksigner.jar’
[ADB] Starting apksigner: ‘C:\Program Files\Java\jdk-19\bin\java.exe’ -Xmx1024M -Xss1m -jar C:\Users\cause\AppData\Local\Android\Sdk\build-tools\33.0.0\lib\apksigner.jar verify –print-certs C:\Users\cause\AppData\Local\Temp\202299-19828-1p2wn9i.yjgq\appium-uiautomator2-server-v4.27.0.apk
[ADB] apksigner stdout: Signer #1 certificate DN: EMAILADDRESS=android@android.com, CN=Android, OU=Android, O=Android, L=Mountain View, ST=California, C=US
[ADB] Signer #1 certificate SHA-256 digest: a40da80a59d170caa950cf15c18c454d47a39b26989d8b640ecd745ba71bf5dc
[ADB] Signer #1 certificate SHA-1 digest: 61ed377e85d386a8dfee6b864bd85b0bfaa5af81
[ADB] Signer #1 certificate MD5 digest: e89b158e4bcf988ebd09eb83f5378e87
[ADB]
[ADB] sha256 hash did match for ‘appium-uiautomator2-server-v4.27.0.apk’
[ADB] ‘C:UserscauseAppDataLocalTemp202299-19828-1p2wn9i.yjgqappium-uiautomator2-server-v4.27.0.apk’ is signed with the default certificate
[ADB] Getting install status for io.appium.uiautomator2.server.test
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell dumpsys package io.appium.uiautomator2.server.test’
[ADB] ‘io.appium.uiautomator2.server.test’ is installed
[ADB] Checking app cert for C:UserscauseAppDataLocalTemp202299-19828-1p2wn9i.yjgqappium-uiautomator2-server-debug-androidTest.apk
[ADB] Starting apksigner: ‘C:\Program Files\Java\jdk-19\bin\java.exe’ -Xmx1024M -Xss1m -jar C:\Users\cause\AppData\Local\Android\Sdk\build-tools\33.0.0\lib\apksigner.jar verify –print-certs C:\Users\cause\AppData\Local\Temp\202299-19828-1p2wn9i.yjgq\appium-uiautomator2-server-debug-androidTest.apk
[ADB] apksigner stdout: Signer #1 certificate DN: EMAILADDRESS=android@android.com, CN=Android, OU=Android, O=Android, L=Mountain View, ST=California, C=US
[ADB] Signer #1 certificate SHA-256 digest: a40da80a59d170caa950cf15c18c454d47a39b26989d8b640ecd745ba71bf5dc
[ADB] Signer #1 certificate SHA-1 digest: 61ed377e85d386a8dfee6b864bd85b0bfaa5af81
[ADB] Signer #1 certificate MD5 digest: e89b158e4bcf988ebd09eb83f5378e87
[ADB]
[ADB] sha256 hash did match for ‘appium-uiautomator2-server-debug-androidTest.apk’
[ADB] ‘C:UserscauseAppDataLocalTemp202299-19828-1p2wn9i.yjgqappium-uiautomator2-server-debug-androidTest.apk’ is signed with the default certificate
[UiAutomator2] Server packages are not going to be (re)installed
[UiAutomator2] Waiting up to 30000ms for services to be available
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell pm list instrumentation’
[UiAutomator2] Instrumentation target ‘io.appium.uiautomator2.server.test/androidx.test.runner.AndroidJUnitRunner’ is available
[ADB] Adding packages [“io.appium.settings”,”io.appium.uiautomator2.server”,”io.appium.uiautomator2.server.test”] to Doze whitelist
[ADB] Got the following command chunks to execute: [[“dumpsys”,”deviceidle”,”whitelist”,”+io.appium.settings”,”;”,”dumpsys”,”deviceidle”,”whitelist”,”+io.appium.uiautomator2.server”,”;”,”dumpsys”,”deviceidle”,”whitelist”,”+io.appium.uiautomator2.server.test”,”;”]]
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell dumpsys deviceidle whitelist +io.appium.settings ; dumpsys deviceidle whitelist +io.appium.uiautomator2.server ; dumpsys deviceidle whitelist +io.appium.uiautomator2.server.test ;’
[UiAutomator2] No app capability. Assuming it is already on the device
[ADB] Getting install status for com.example.yeshasprabhakar.todo1.0
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell dumpsys package com.example.yeshasprabhakar.todo1.0’
[ADB] ‘com.example.yeshasprabhakar.todo1.0’ is not installed
[UiAutomator2] Deleting UiAutomator2 session
[UiAutomator2] Deleting UiAutomator2 server session
[WD Proxy] Matched ‘/’ to command name ‘deleteSession’
[UiAutomator2] Did not get confirmation UiAutomator2 deleteSession worked; Error was: UnknownError: An unknown server-side error occurred while processing the command. Original error: Trying to proxy a session command without session id
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell am force-stop com.example.yeshasprabhakar.todo1.0’
[Logcat] Stopping logcat capture
[ADB] Removing forwarded port socket connection: 8200
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 forward –remove tcp:8200’
[UiAutomator2] Restoring hidden api policy to the device default configuration
[ADB] Running ‘C:UserscauseAppDataLocalAndroidSdkplatform-toolsadb.exe -P 5037 -s 22X0220428007340 shell ‘settings delete global hidden_api_policy_pre_p_apps;settings delete global hidden_api_policy_p_apps;settings delete global hidden_api_policy”
[BaseDriver] Event ‘newSessionStarted’ logged at 1665348801035 (22:53:21 GMT+0200 (Mitteleuropäische Sommerzeit))
[W3C] Encountered internal error running command: Error: ‘app’ option is required for reinstall
[W3C] at Object.resetApp (C:Program FilesAppium Server GUIresourcesappnode_modulesappiumnode_modulesappium-android-driverlibandroid-helpers.js:405:11)
[W3C] at AndroidUiautomator2Driver.initAUT (C:Program FilesAppium Server GUIresourcesappnode_modulesappiumnode_modulesappium-uiautomator2-driverlibdriver.js:546:9)
[W3C] at AndroidUiautomator2Driver.startUiAutomator2Session (C:Program FilesAppium Server GUIresourcesappnode_modulesappiumnode_modulesappium-uiautomator2-driverlibdriver.js:408:5)
[W3C] at AndroidUiautomator2Driver.createSession (C:Program FilesAppium Server GUIresourcesappnode_modulesappiumnode_modulesappium-uiautomator2-driverlibdriver.js:229:7)
[W3C] at AppiumDriver.createSession (C:Program FilesAppium Server GUIresourcesappnode_modulesappiumlibappium.js:387:35)
[HTTP] <– POST /wd/hub/session 500 5562 ms – 663
[HTTP]