Subdomain takeover vulnerability is not new in cybersecurity space but it’s pretty much effective today’s time also. In the bug bounty field subdomain takeover vulnerability reports are rapidly growing.
The basic premise of a subdomain takeover is a host that points to a particular service not currently in use, which an adversary can use to serve content on the vulnerable subdomain by setting up an account on the third-party service. As an ethical hacker and a security analyst, We deal with this type of issue on a regularly.
What is Subdomain Takeover Vulnerability
For beginners subdomain takeover idea may not clear, so we are explaining it in very easy way.
Suppose our target is example.com and they are running a bug bounty program, because we just can’t go and takeover any other’s subdomain because it will be unethical. So we assume that example.com is running bug bounty program and we find a subdomain named subdomain.example.com, this subdomain shows 404 error.
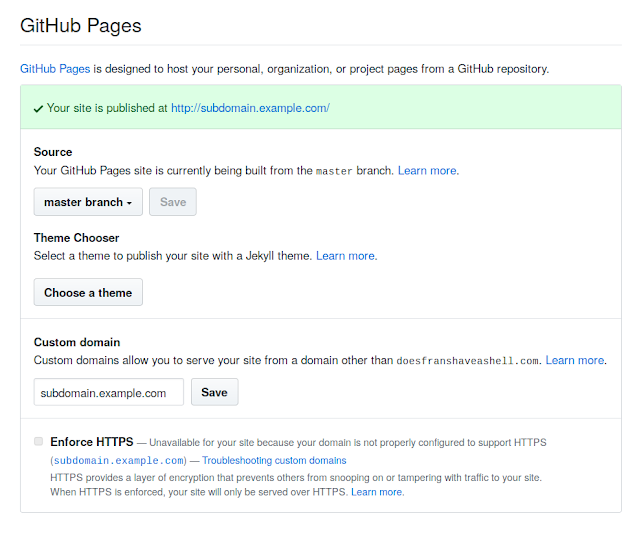
Now this subdomain is pointing to some another services. For an example we assume that this subdomain is pointing to GitHub Pages.
How do we know that it is pointing to GitHub Pages? Well, here we need to look on it’s DNS settings (in this case we can see GitHub clearly, but may be in other cases we need to check DNS).
We can run following command to check the host of subdomains:
host subdomain.example.comHere we will get the IP address of the subdomain then we can check from where this IP address belongs by using following command:
whois <IP Address>|grep "OrgName"Most of cybersecurity experts starts senses start tingling at this point. This 404 subdomain page indicates that no content is being served under the top-level directory and that we should attempt to add this subdomain to oue personal GitHub repository.
Broken Link Hijacking
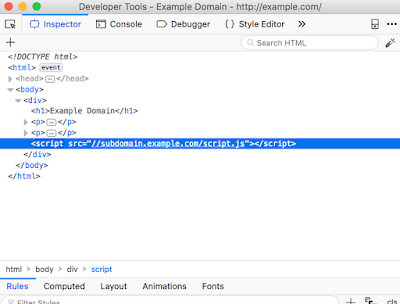
There are another way to takeover subdomains. It is referred as ‘Broken Link hijacking‘. These are vulnerable subdomains which do not necessarily belong to the target but they are used to serve content on the target’s website. This means that a resource is being imported on the target page, for an example, via a little fault in JavaScript code and the cybersecurity expert can claim the subdomain from which the resource is being imported.
Hijacking a host that is used somewhere on the page can ultimately lead to stored cross-site scripting (XSS), since the adversary can load arbitrary client-side code on the target page. The reason why we wanted to list this issue in this article, is to highlight the fact that, as a cybersecurity expert, We don’t want to only restrict ourselves to subdomains on our target host. We can easily expand our scope by inspecting source code and mapping out all the hosts that the target relies on.
These are the basic principal of “Subdomain Takeover Vulnerability“. This is very important for Bug-Bounty hunters. We tried to explain this in very easy language.
Not only GitHub Pages we can do it if the 404 subdomain is pointed to AWS, Heroku, Readme and other services. We got a very informative article about subdomain takeover.
Love our article? Make sure to follow us on Twitter and GitHub, we post article updates there. To join our KaliLinuxIn family, join our Telegram Group & Whatsapp Channel. We are striving to build a community for Linux and cybersecurity. For anything we always happy to help everyone on the comment section. As we know our comment section is always open to everyone. We read each and every comment and we always reply.
Source: Read More