

Intrusion detection systems (IDS) encounter significant challenges in detecting zero-day or unknown cyberattacks, which are not included in the training data. These attacks do not have any identifiable pattern and cannot be easily detected by traditional techniques. The lack of annotated samples of attacks, the highly dynamic nature of attack methodologies, and the problem of high-dimensional datasets further pose a challenge to the problem. Such vulnerabilities tend to increase with the expansion of networks, especially in IoT and Industrial IoT ecosystems; therefore, more advanced IDS frameworks are required to adapt to dynamic network environments and provide robust protection.
Conventional IDS techniques often rely on supervised learning models, requiring extensive labeled datasets containing benign and attack samples. Such methods are useful for detecting attacks that have occurred in the past but depend on the availability of such historical datasets, thus limiting their capability to detect zero-day vulnerabilities. Other approaches, such as OCC techniques like One-Class SVM and Isolation Forest, are based on characterizing normal traffic patterns without using labeled attack data. However, these approaches face high-dimensional datasets and, in turn, very high false-negative rates and, therefore, have limited applicability in real-world dynamic environments.
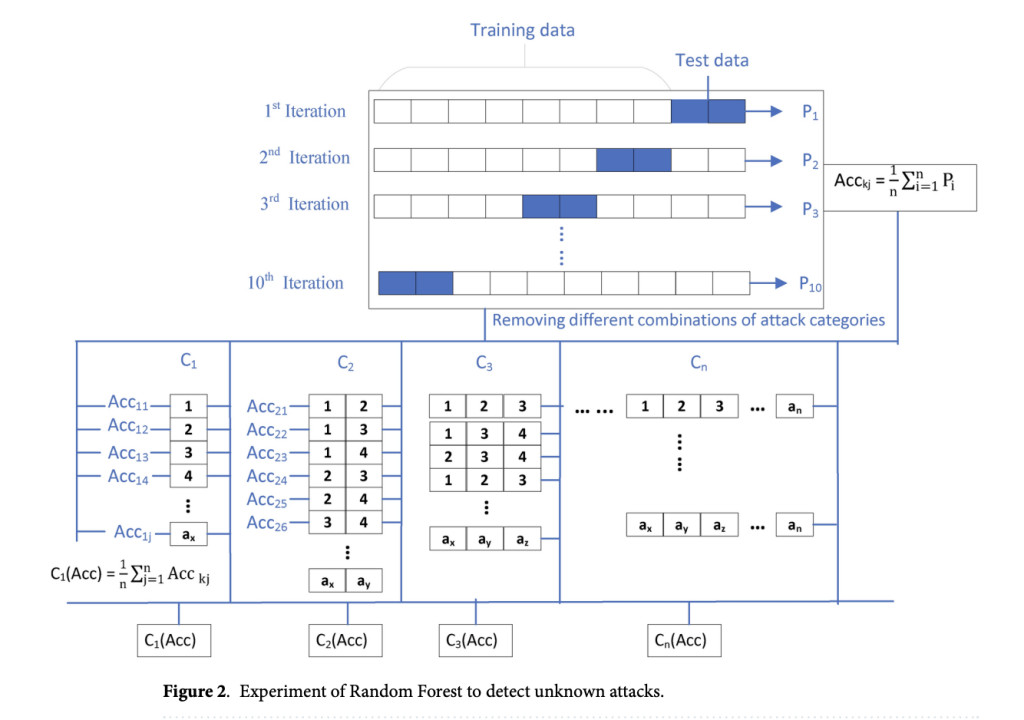
Researchers introduced a semi-supervised framework built around the usfAD (Unsupervised Stochastic Forest Anomaly Detector) algorithm to address these limitations. In other words, this state-of-the-art method can evade the constraints of requiring labeled attack data, while still bringing the anomalies in legitimate traffic forward. The synthetic data augmentation method, which generates noise uniformly distributed and tagged as attack data, extends the feature space and enables generalizing the system to unknown patterns as well. In addition, ensemble models combining different OCC techniques improve both robustness and accuracy significantly by drastically reducing false negatives. These improvements make the framework very effective for zero-day attack detection in a range of dynamic and varied network contexts.
The usfAD algorithm, a key component of this framework, builds on isolation forest-like structures to identify anomalies without relying on density or distance calculations, making it efficient for large-scale, high-dimensional datasets. The system also has dynamic thresholding based on statistical properties of training data, such as mean and standard deviation.
Synthetic data augmentation effectively tackles the issue of limited attack samples by generating artificially created instances that mimic attack characteristics, thereby improving the system’s detection proficiency. A comprehensive assessment of the framework was conducted utilizing ten benchmark datasets, among which NSL-KDD and CIC-DDoS2019 stand out as representations of varied attack contexts and network environments. Performance evaluation employed metrics including accuracy, precision, recall, and F1-score, while stratified cross-validation was implemented to guarantee a robust assessment.
The framework showed outstanding performance on a range of benchmark datasets, significantly outperforming traditional approaches. It achieved 95.92% accuracy on NSL-KDD and 99.43% on ToN-IoT-Network, demonstrating its robustness in handling complex and high-dimensional data. Ensemble configurations, particularly “Ensemble-Any Two,†achieved an optimal balance between sensitivity and specificity, reducing false positives while maintaining detection rates. The findings highlight the flexibility and dependability of the methodology in detecting zero-day threats in various contexts, thereby establishing it as a strong solution for contemporary cybersecurity issues.
This advanced IDS framework overcomes the limitations of existing methods by leveraging the usfAD algorithm, ensemble strategies, and synthetic data augmentation. Removing dependence on labeled attack samples and using adaptive thresholding, the method provides excellent detection accuracy and adaptability to evolving threats. Performance on various datasets shows it can redefine standards for detecting zero-day attacks, creating an effective, scalable, and efficient means of safeguarding modern networks against dynamic and complex cyber threats.
Check out the Paper. All credit for this research goes to the researchers of this project. Also, don’t forget to follow us on Twitter and join our Telegram Channel and LinkedIn Group. If you like our work, you will love our newsletter.. Don’t Forget to join our 55k+ ML SubReddit.
The post Enhanced IDS Framework with usfAD for Detecting Unknown Attacks appeared first on MarkTechPost.
Source: Read MoreÂ



 ‘
‘