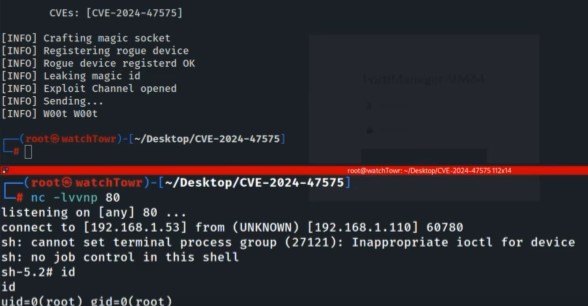
The ‘FortiJump’ vulnerability in Fortinet’s FortiManager management platform may not have been completely fixed by the company’s patch issued last month.
A screen recording posted to X (formerly known as Twitter) today by WatchTowr suggested that the vulnerability – CVE-2024-47575 – can still be exploited.
Cyble threat intelligence researchers reported last week that 62,000 vulnerable FortiManager instances were exposed to the internet, indicating significant enterprise exposure to this 9.8-severity vulnerability.
“[D]espite all the buzz about FortiManager – the saga is about to continue,†WatchTowr said. “Please, remove this from the Internet *even if fully patched*â€
The FortiJump Saga Continues
Reports of an exploited zero-day vulnerability in FortiManager were circulating more than a week before the CVE was officially reported on October 23.
That created confusion among security researchers and even some FortiManager customers, but Cyble noted that Fortinet had sent clients an advisory a week before the vulnerability was officially disclosed, and that communication contained recommended mitigations too. However, some FortiManager customers said they hadn’t received that communication, suggesting a need for Fortinet to revisit its advisory procedures.
In a blog post that was published the same day as the CVE, Mandiant said it had been working with Fortinet on the issue and noted that the vulnerability – classified as a “missing authentication for critical function†weakness (CWE-306) – had been exploited more than 50 times since at least late June by a new threat actor dubbed “UNC5820.â€
“UNC5820 staged and exfiltrated the configuration data of the FortiGate devices managed by the exploited FortiManager,†Mandiant said. “This data contains detailed configuration information of the managed appliances as well as the users and their FortiOS256-hashed passwords. This data could be used by UNC5820 to further compromise the FortiManager, move laterally to the managed Fortinet devices, and ultimately target the enterprise environment.â€
The post noted that data sources analyzed by the investigators “did not record the specific requests that the threat actor used to leverage the FortiManager vulnerability. Additionally, at this stage of our investigations there is no evidence that UNC5820 leveraged the obtained configuration data to move laterally and further compromise the environment.â€
Still, a commenter on a Reddit thread discussing the latest revelation noted, “For everyone running one anyway the best solution is rebuilding it from scratch and never connect the instance to the internet, at least put something in front of it and only let trusted IPs connect.â€
Also read: Nearly 1 Million Vulnerable Fortinet, SonicWall Devices Exposed to the Web
Fortinet Has Updated FortiJump Advisory 8 Times
The Cyber Express asked Fortinet for any comment or mitigations in response to WatchTowr’s claim that FortiManager remains vulnerable, but no response had been received as of publication time.
CISA issued an alert on October 30 stating that Fortinet had updated its guidance (PSIRT FG-IR-24-423) on the vulnerability, which includes a number of allowlisting and denylisting steps to prevent the addition and registration of unauthorized devices in addition to recovery methods. According to Fortinet’s timeline at the bottom of the guidance page, the most substantive changes to the document appeared to have occurred between Oct. 23-28:
- 2024-10-23: Add FortiManager Cloud fixes
- 2024-10-24: Added workarounds to block the addition of unauthorized devices via syslog or FDS
- 2024-10-24: Added 195.85.114.78 in IoCs
- 2024-10-25: Added note about log entries IoCs
- 2024-10-28: Added link to “Best Practices for Maintaining Secure Credentials”
- 2024-10-28: Added note in workaround 1. (FMG Cloud recommended workaround)
- 2024-10-30: Added IoCs (4 IP addresses and 1 SN)
- 2024-11-04: Removed duplicate IP addresses
Â
Source: Read More