Cyble researchers have uncovered a new loader builder and obfuscation tool that has largely gone undetected by security tools.
Cyble Research and Intelligence Labs (CRIL) researchers detailed their findings in a blog post today. The “MisterioLNK†loader builder, found on GitHub, “presents a significant challenge to security defenses, as files generated by this tool currently exhibit minimal or zero detection rates by conventional security systems,†the researchers wrote.
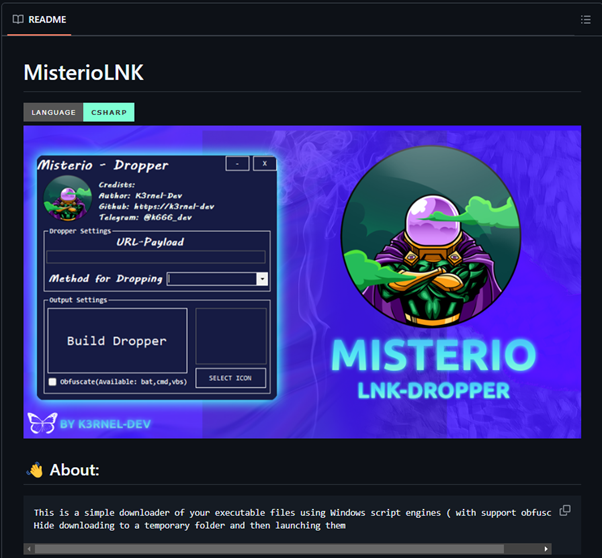
The MisterioLNK open-source loader builder leverages Windows script engines to execute malicious payloads while employing obfuscation. “It is crafted to operate discreetly, downloading files into temporary directories before launching them, thereby enhancing its evasive capabilities and making detection by traditional security measures difficult,†Cyble said.
MisterioLNK supports five loader methods—HTA, BAT, CMD, VBS, and LNK— along with obfuscation methods for VBS, CMD, and BAT, with plans to add support for HTA obfuscation. The project is currently in beta, and the developer “disclaims any responsibility for illegal activities conducted using this software.â€
Threat Actors Are Using MisterioLNK to Deploy Malware
While security tools are struggling to detect the loader builder, cybercriminals have apparently had no problem finding it. The Cyble researchers said threat actors (TAs) have already started using MisterioLNK to generate obfuscated files for deploying malware such as Remcos RAT, DC RAT, and BlankStealer. “Alarmingly, these loaders are largely evading detection, with many remaining undetected by most security vendors,†the report said.
The researchers generated all combinations of loader files to evaluate their ability to evade detection. Out of six files, only one was detected with 16 detections, two files had one detection each, and three files showed zero detections. Security vendors are having some success detecting LNK and obfuscated VBS loaders produced by the builder, but the detection rates for BAT, CMD, HTA, and VBS loader files were low (image below).
MisterioLNK detections on VirusTotal (Cyble)Misterio’s Loader Builder, Obfuscator and LNK Modules
Misterio.exe, a .NET-based tool, consists of two primary modules: a loader builder and an obfuscator, Cyble said.
“The builder accepts a URL hosting a malicious second-stage payload and generates BAT, CMD, HTA, LNK, or VBS files based on the user’s selection,†the researchers said. Those files are designed to connect to the URL, download the payload, and execute it.
The BAT/CMD loader is designed to download files from specified URLs using the ‘curl` command and then executing the downloaded files. The resulting script is saved with a custom file icon for increased deception, and obfuscation adds an additional layer of concealment.
The HTA (HTML Application) loader uses JavaScript and ActiveX objects to execute commands for downloading and running files. The HTA obfuscation feature is currently inactive but could be implemented in the future.
The VBS Loader uses shell object commands for downloading and executing the target file, and also includes an obfuscation process.
The LNK Loader Builder creates a shortcut file (.lnk) that when executed triggers a command to download and run the target file.
“Together, these modules form a powerful toolkit for generating and concealing scripts that can deliver and execute payloads with minimal detection,†the researchers said.
Cyble’s Recommendations
Security teams should ensure that their security solutions can recognize and detect the obfuscation patterns and script formats generated by MisterioLNK Builder, and add restriction policies and behavioral detection strategies to their defenses too.
The full Cyble blog digs further into MisterioLNK’s capabilities and also lists MITRE ATT&CK Techniques and indicators of compromise (IoCs).
Source: Read More