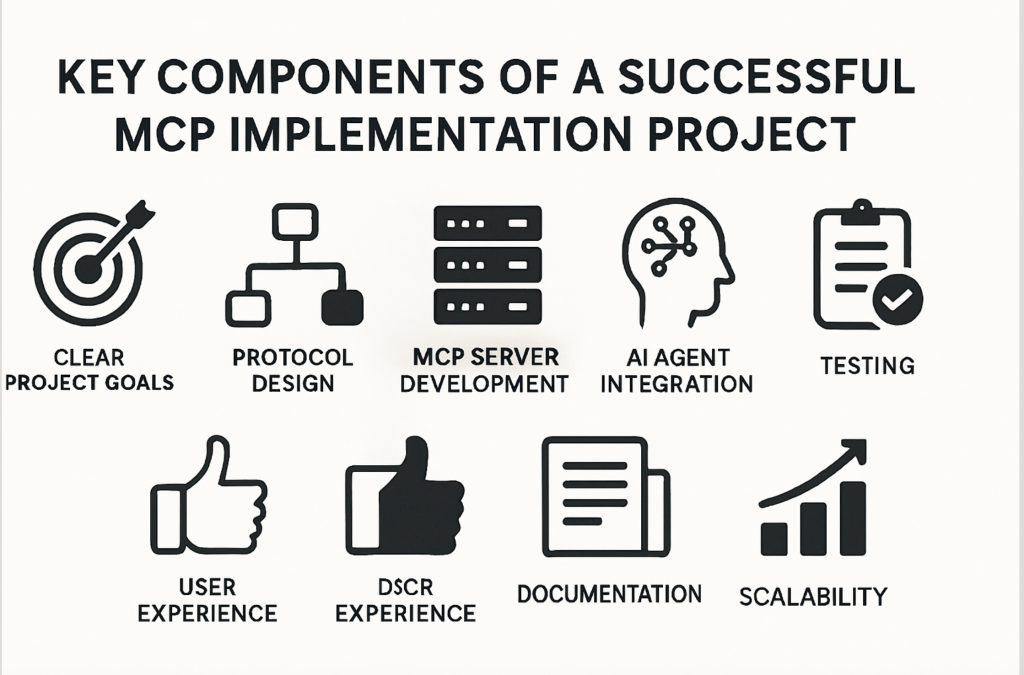
The Model Context Protocol (MCP) is changing how intelligent agents interact with backend services, applications, and data. A successful MCP implementation project hinges on much more than writing protocol-compliant code. Systematic adoption involves architecture, security, user experience, and operational rigor. Here’s a data-driven look at essential components that ensure MCP projects deliver value and resilience in production environments.
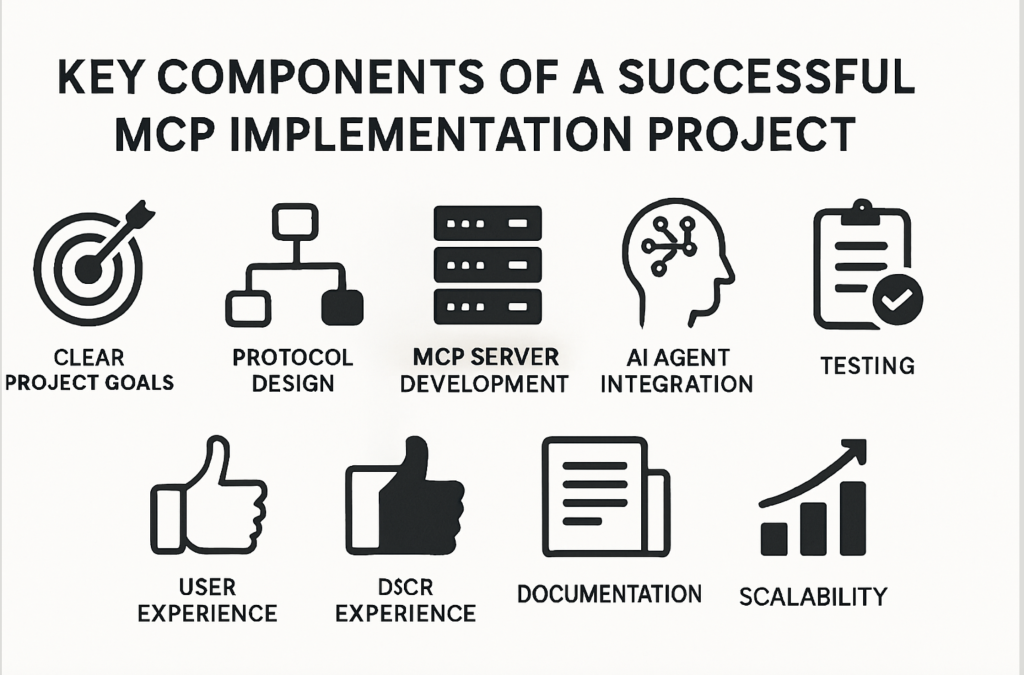
1. Clear Project Goals, Use Cases, and Stakeholder Buy-In
- Define business and technical problems you’re solving with MCP: Example use cases include multi-app workflow automation, AI-powered content generation, or agent-based DevOps operations.
- Engage users and IT early: Successful MCP teams conduct requirements workshops, interviews, and prioritize quick pilot wins.
2. Protocol, Integration, and Architecture Design
- Mapping AI agent, MCP middleware, and target applications: The principle of loose coupling (stateless API endpoints) is key. Most advanced teams use HTTP/2 or websockets for real-time data push, avoiding heavy polling and reducing latency by up to 60% in agent workflows.
- Contextual payloads: Embedding rich context (user, task, permissions) in protocol messages leads to higher agent accuracy and fewer ambiguous requests—critical for safety and compliance.
3. Robust Security & Permissions
Data Point: A 2024 GitLab DevSecOps survey found 44% of teams place security as the #1 blocker to AI workflow adoption.
- Authentication: OAuth 2.0, JWT tokens, or mutual TLS remain best practices for MCP endpoints.
- Granular permissions: Implement role-based access control (RBAC), with audit logging for every AI-triggered action.
- User consent & transparency: End users should be able to view, approve, and revoke MCP access to data and controls.
4. MCP Server Development & Extensibility
- Reusable, scalable, and stateless MCP servers: Architect servers that scale horizontally (containerized, cloud-native). Container orchestration (Kubernetes, Docker Swarm) is common for elastic scaling.
- Open API definitions: Use OpenAPI/Swagger to document endpoints, enabling rapid onboarding of AI agents and developers.
- Extensibility: Modular plugin or handler architecture supports future integrations without core refactoring—a trait in the most successful MCP deployments.
5. AI Agent Integration, Memory, and Reasoning
- Contextual memory: Store recent actions (with expiry) or full session transcripts for auditability and continuity.
- Failure handling: Implement structured error payloads and fallback logic—critical for scenarios where agent actions are irreversible or costly.
6. Comprehensive Testing and Validation
- Automated test suites: Use mocks and stubs for MCP integration points. Cover input validation, error propagation, and edge cases.
- User acceptance testing: Pilot workflows with real users, collect telemetry, and iterate quickly based on feedback.
7. User Experience and Feedback Mechanisms
- Conversational UX: For agent-driven flows, natural language feedback and confirmations are critical. Well-designed systems show intent recognition rates >90% (Google Dialogflow research).
- Continuous feedback loop: Integrate NPS surveys, bug reporting, and feature requests directly into the MCP-enabled tools.
8. Documentation and Training
- Comprehensive, up-to-date documentation: Top-performing teams publish API docs, setup guides, and integration playbooks.
- Hands-on training: Interactive demos, sample code, and “office hours” help drive adoption among developers and non-developers alike.
9. Monitoring, Logging, and Maintenance
- Dashboards: Real-time monitoring of agent initiations, action completions, and API errors.
- Automated alerting: Set up threshold-based alerts for critical paths (e.g., failed authentication spikes).
- Maintenance routines: Schedule regular reviews of dependency versions, security policies, and context/permissions scope.
10. Scalability and Extensibility
- Horizontal scaling: Use managed container services or function-as-a-service models for rapid scale-out and cost efficiency.
- Consistent versioning: Adopt semantic versioning and maintain backward compatibility—enabling agents (and users) to operate during upgrades.
- Plug-in architecture: Future-proofing your MCP implementation with plug-in compatible modules allows for the integration of new tools, agents, or services with minimal friction.
Conclusion
A successful MCP implementation is as much about robust architecture and security as it is about creating seamless, valuable user experiences. Teams that invest in clear vision, security, comprehensive testing, and continuous feedback are best positioned to harness MCP for transformative AI-powered workflows and applications. With the protocol ecosystem maturing rapidly and examples from industry adoption emerging each month, the playbook above helps ensure MCP projects deliver on their intelligent automation promise.
The post Key Factors That Drive Successful MCP Implementation and Adoption appeared first on MarkTechPost.
Source: Read MoreÂ