Nearly a year after its troubled initial rollout, Microsoft Recall is back.
Microsoft announced in an April 25 blog post that it will begin rolling out the Windows Recall feature on Copilot+ PCs, claiming much-improved security for the screen recording tool.
Security and privacy issues do seem to have improved markedly over early versions of Recall, which had resulted in a backlash that caused Microsoft to delay the product for further testing and development.
Despite the improvements, some significant security issues remain, particularly involving biometrics and sensitive data recording, which should prompt users with sensitive data use cases to proceed with caution.
Recall is now available for Copilot+ PCs via the April 2025 Windows non-security preview update, and Microsoft will roll out Recall and other new features via controlled feature rollout (CFR) over the next month.
Microsoft Recall Security Issues Remain
Independent security researcher (and former Microsoft employee) Kevin Beaumont started the initial Recall concerns in early June 2024, when his work was first reported by The Cyber Express.
In a blog post last week just before Microsoft’s Recall rollout announcement, Beaumont gave Microsoft credit for improving Recall even as he noted that some concerns remain.
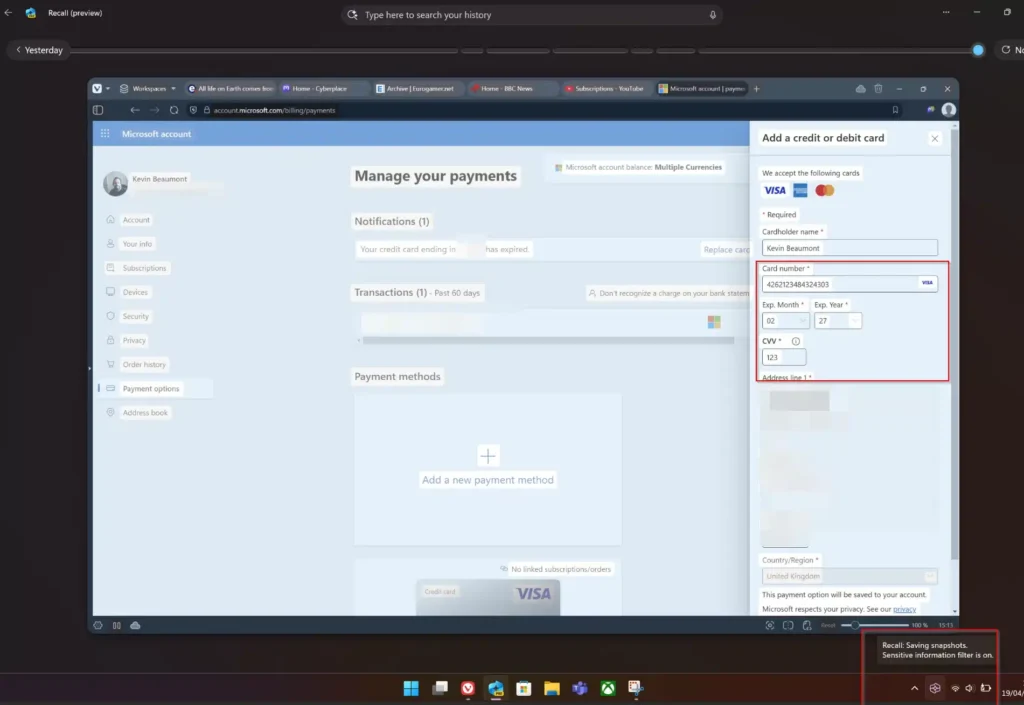
“Microsoft has made serious efforts to try to secure Recall,” Beaumont said. Recall is now opt-in rather than enabled by default, the SQLite database at the heart of Recall is now encrypted (image below), and by default Recall attempts to filter and exclude sensitive information like credit cards.

However, Beaumont noted that a few significant security and privacy issues remain. For one, biometrics is used only to set up Recall; after that, just knowing (or guessing) the user’s PIN would be enough to access it.
“The biometrics is just the initial onboarding,” Beaumont wrote. “It doesn’t apply afterwards. I think this is a big miss by Microsoft — biometrics should be required every time Recall is accessed, I think, as otherwise people will have a false sense of security.”
The sensitive data filter doesn’t work reliably, he said, noting that it recorded a fake credit card number he typed in while using the Vivaldi browser.
“You basically need to be careful to review what Recall is recording, which is difficult when it records everything you do,” he said. “The best advice I can give is pause Recall before shopping online to ensure it isn’t recording, then reenable it afterwards.”
Beaumont raised one issue that many probably haven’t considered – if you’re communicating with a Copilot+ user over a private messaging app, it’s possible that conversations you think disappeared or were deleted on apps like Signal, WhatsApp or Teams have been captured by Recall. Video conferencing and even remote desktop sessions are captured by Recall, he said.
“I would recommend that if you’re talking to somebody about something sensitive who is using a Windows PC, that in the future you check if they have Recall enabled first,” Beaumont said.
He also noted that it remains to be seen how secure the encrypted database is.
Who Shouldn’t Use Microsoft Recall?
Beaumont said people in certain circumstances or professions shouldn’t use Recall. Those include:
- People in domestic violence situations or those with issues with a personal relationship
- Journalists and their confidential sources
- Minority at-risk groups
- Politically exposed people
- Companies that haven’t properly assessed Recall’s privacy and security risks
- People crossing borders “into countries hostile to civil liberties.”
Source: Read More