When learning about cybersecurity, you’ll quickly realize that some vulnerabilities are more dangerous than others. One of the most serious ones is called command execution.
Hackers use it to run harmful commands on a system, gain access to sensitive data, take control of servers, or even shut down entire networks.
But how does it really work? And why is it such a big problem? Let’s break it down in simple terms.
What Is Command Execution?
Imagine a computer program that allows you to input something — like a website address or a file name — and then perform an action based on that input.
For example, a web tool might allow you to type in a domain name and then run a “ping†command to check if the site is online. Sounds useful, right?
Here’s where the problem starts: if the program doesn’t properly control or clean up what you enter, a hacker could type something unexpected — like a command that deletes all files on the system.
Instead of just doing what the program was designed to do, the hacker’s command gets executed as if it were legitimate.
Let’s look at an example of bad code:
import os
def ping_host(domain):
os.system(f"ping {domain}")
Here’s what’s happening:
You enter a domain like “example.comâ€.
The program runs the
pingcommand on the system, which sends test messages to “example.com” to check if it’s reachable.
The issue is that the program doesn’t limit what you can enter. If someone malicious enters something like example.com && rm -rf /, it might execute both the ping command and the rm -rf / command, which wipes out all the files on the computer.
Below is an example of injecting the hostname command which displays the system information.
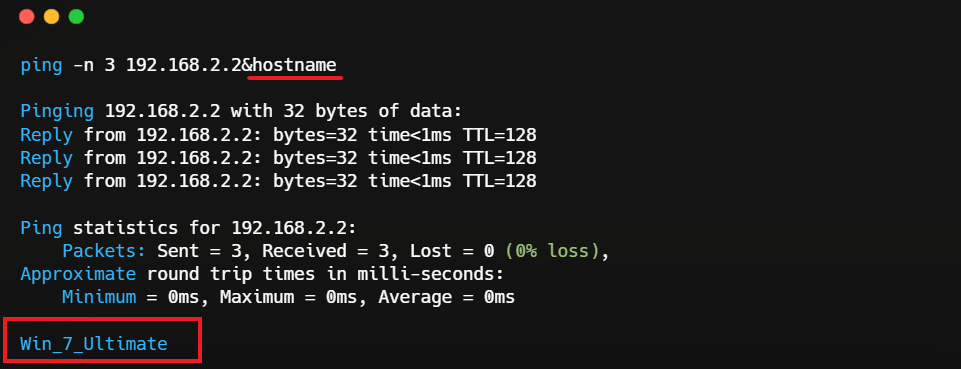
That’s command execution in a nutshell — when user input is misused to run unplanned system commands.
Types of Command Execution Attacks
There are two main ways hackers use command execution to attack systems: command injection and remote code execution (RCE).
Command Injection
This is the easier type of attack. Hackers “inject†extra commands into a program by adding unexpected text to a field that accepts user input. The example above, where a hacker adds && rm -rf / to the domain name, is a classic example of command injection.
Hackers use this technique to read sensitive files, delete important data, or steal information from the system.
Remote Code Execution (RCE)
This is the more serious version. With RCE, a hacker doesn’t just run commands — they can upload and run entire scripts or programs on the system.
It’s like giving a hacker the keys to your computer, letting them do whatever they want.
For example, imagine an attacker uploads a small program that secretly listens to their commands. They could then use that program to install ransomware, spy on users, or take full control of the system.
Real-Life Examples of Command Execution Attacks
Let’s look at a couple of real-world cases where command execution vulnerabilities caused major damage.
The Shellshock Bug (2014)
The Shellshock bug was a massive vulnerability found in the Bash shell (a program used in many Unix-based systems). Hackers could inject commands into environment variables, tricking the system into running them.
Shellshock allowed attackers to take over servers, steal data, and launch large-scale attacks. This vulnerability was so serious that it affected millions of systems worldwide and required immediate patches.
Cisco Security Flaw (2020)
In 2020, a vulnerability was found in Cisco’s firewall devices. This flaw let hackers execute commands on the devices remotely, gaining full control of them.
Since these firewalls are used to protect sensitive networks, the vulnerability posed a major risk to businesses and organizations.
How to Protect Yourself From Command Execution Attacks
Protecting yourself from command execution vulnerabilities is all about following good practices.
Always Sanitize User Input—Think of every user input as a potential threat. For example, if a form asks for a name, a hacker might input something like
rm -rf /. To stop this, you can use functions that strip out dangerous characters.Avoid Running System Commands—Running commands directly from your application can be risky. Instead of using something like
os.system('ls')in Python, usesubprocess.run()withshell=False. This way, even if someone tries to inject harmful commands, they won’t run because the shell isn’t involved.Limit What Programs Can Do—Make sure your programs only have the permissions they truly need. For example, if an application doesn’t need to modify system files, don’t let it have write access to them.
Keep Everything Updated—Hackers love old software because it’s like a broken lock. By updating your operating system and libraries regularly, you patch known vulnerabilities. For instance, the infamous Shellshock bug in Bash affected outdated systems but was fixed in later versions.
Test for Vulnerabilities—Before someone else finds the holes in your system, test it yourself. Tools like Burp Suite or OWASP ZAP are helpful for automated scanning. For example, you can simulate attacks to see how your web app reacts and fix issues before they’re exploited.
Watch Your Logs—Logs are like security cameras for your server. If you see something odd, like a lot of failed login attempts or commands you didn’t authorize, it’s a red flag. Set up alerts to catch these signs early.
By following these best practices, you’ll make your systems much harder to break into.
Summary
Command execution vulnerabilities are one of the most powerful tools hackers can use. By exploiting them, attackers can completely control a system, steal sensitive information, or cause massive damage. Understanding this vulnerability is a key step in learning how to defend systems.
Want some real-world experience in cybersecurity? Try our five-day Hacker’s Headstart boot camp. Happy hacking!
Source: freeCodeCamp Programming Tutorials: Python, JavaScript, Git & MoreÂ



