Cyble Research and Intelligence Labs (CRIL) researchers have uncovered an active campaign exploiting a Microsoft SmartScreen vulnerability to inject infostealers into users’ machines.
Microsoft released a patch for the SmartScreen vulnerability (CVE-2024-21412) in February and CISA even added it to its known exploited vulnerabilities catalog, but apparently the patch has seen limited deployment, as Cyble said the campaign is targeting users in multiple regions, including Spain, the U.S., and Australia.
Another SmartScreen vulnerability (CVE-2024-29988) was patched in April.
Microsoft SmartScreen Vulnerability Exploited by Phishing
The campaign begins with phishing lures related to healthcare insurance schemes, transportation notices, and tax-related communications to trick users into downloading malicious payloads. The spam emails contain a link that redirects users to a WebDAV share using a search protocol to deceive them into executing a malicious internet shortcut file, the Cyble researchers said.
The multi-stage attack that follows utilizes legitimate tools such as forfiles.exe, PowerShell, mshta, and other trusted files to circumvent security measures, and then DLL sideloading and IDATLoader inject the final payload into explorer.exe.
The campaign delivers Lumma and Meduza Stealer as its final payloads.
Zero-Day Attack Discovered in January
The Zero Day Initiative (ZDI) uncovered a sophisticated DarkGate campaign in mid-January that was exploiting the vulnerability through fake software installers. The APT group Water Hydra has also been leveraging CVE-2024-21412 in a targeted campaign against financial market traders, bypassing SmartScreen to deploy the DarkMe remote access trojan (RAT).
In the latest campaign, the Cyble researchers said threat actors (TAs) have been exploiting the vulnerability to bypass Microsoft Defender SmartScreen and deploy payloads on victims’ systems.
The image below shows the sophisticated infection chain observed by the Cyble researchers in the latest attacks.
Microsoft SmartScreen vulnerability attack chain (source: Cyble blog)Lure documents used in the campaign target Spanish taxpayers, transportation companies with emails purportedly from the U.S. Department of Transportation, and individuals in Australia by mimicking official Medicare enrollment forms.
Sophisticated Attack Chain
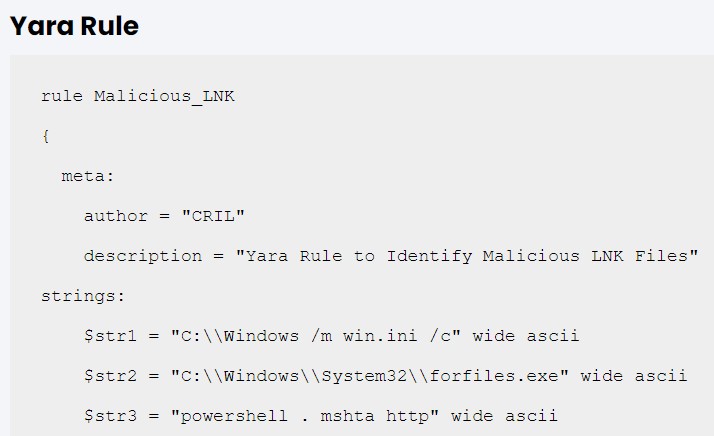
Upon execution, the malicious LNK file triggers the forfiles utility, a legitimate Windows executable designed for batch processing files, the researchers said. If the utility successfully finds the “win.ini†file within the C:Windows directory, forfiles.exe proceeds to execute a PowerShell command leveraging “mshta.exe†to execute a malicious file hosted on a remote server.
The hosted file is named “dialer.exeâ€, which has been altered to include embedded malicious JavaScript that utilizes the String.fromCharCode() method to decode and execute a PowerShell Script. That script decrypts the AES-encrypted blocks to load yet another PowerShell script, which downloads the lure document and another 7z installer file from the remote server and saves them to C:UsersuserAppDataRoaming. Upon successful download, the PowerShell script opens the lure document and executes the installer file.
The installer file then drops additional files, including clean files, dependency DLLs, a malicious DLL for side-loading, and an encrypted IDAT loader, the Cyble researchers wrote.
After placing all the files in the %appdata% directory, the installer file begins DLL side-loading by launching a legitimate file. “This legitimate file then loads a malicious DLL, which retrieves the content of the IDAT loader, decrypts it, and injects the payload into explorer.exe,†the researchers said. “In this campaign, the injected content, recognized as Lumma and Mdeuza Stealer, subsequently carries out malicious operations on compromised systems.â€
‘Increasingly Dynamic and Dangerous Threat Landscape’
The Cyble researchers said the recent surge in the exploitation of CVE-2024-21412, along with the adoption of sophisticated techniques such as DLL sideloading and IDATLoader combinations, “highlights how cyber threats continue to evolve in an increasingly dynamic and dangerous threat landscape.â€
Malware-as-a-Service (MaaS) could amplify that trend by allowing malicious actors to deploy advanced tools more readily, they said.
The researchers recommended a number of cybersecurity controls to help fight these sophisticated threats:
Advanced email filtering solutions can help detect and block malicious attachments and links, adding extra protection on top of cybersecurity training for end users.
The forfiles utility should be monitored and restricted, and the execution of scripting languages on user workstations and servers should be disabled or restricted if they are not essential for legitimate purposes.
Application whitelisting will help ensure that only approved and trusted applications and DLLs can execute on your systems.
Network segmentation can protect critical workloads and limit the spread of malware within an organization.
The Cyble blog also includes MITRE ATT&CK Techniques, Indicators of Compromise (IoCs) and a YARA detection rule.
Source: Read More