Laravel is famous for Eloquent ORM which typically works with relational databases like MySQL. But what if you want to…
Libraries & Frameworks
How do I detect text inside of this, this is HTML & this is XPath. I tried
HTML
<span class=”messageText”>Hello.</span>
XPath
//*[@id=”liveAgentChatLogText”]/span[22]/span[2]
I tried with this but it didn’t work, it said no such element found.
driver.find_element(By.XPATH, ‘//*[@id=”liveAgentChatLogText”]//*[contains(string(.), “Hello”)]’)
I have two loop controllers inside a simple controller.
But it stops running after the execution of first loop even if the results is successful.
Structure is given below
ThreadGroup
Simple Controller 1
HTTP Request
Loop Controller1 (Loops 10 times with a CSV file)
Loop Controller2 (Loops 25 times with another CSV file)
Simple Controller 2
HTTP Request 1
HTTP Request 2
HTTP Request 3
Loop Controller 3 (Loops 15 times 3rd CSV file)
But execution stops after completing Loop controller 2. It doesn’t go for the Loop controller 2 or doesn’t start Simple Controller 2. If Simple Controller 1 is disabled, it will run Simple Controller 2 successfully.
Any suggestion will be of great help.
Thanks
I’m working on a project with www.NJMLS.com. I’m trying to extract email of agent name “Edward An”:
import dryscrape as d
d.start_xvfb()
br = d.Session()
br.visit(‘http://www.njmls.com/members/index.cfm?action=dsp.results&city=&county=&nametype=firstname&name=Edward&x=70&y=33’)
#open url and try to extract the email of Edward An
How to get email of “Edward An”? If I try:
for x in br.xpath(“//*[@class = ‘realtor-info’]/*”)
# selecting all elements in <div class=”realtor-info”>….</div>
if “Edward An” in x:
print x[‘herf’]
#Not responding
I am not getting any response.
What’s wrong with my script?
if “Edward An” in x.text()
print x
This is also not working. Still there is no error and no response.
<svg aria-label=”Unlike” class=”_8-yf5 ” color=”#ed4956″ fill=”#ed4956″ height=”24″ role=”img” viewBox=”0 0 48 48″ width=”24″><path d=”M34.6 3.1c-4.5 0-7.9 1.8-10.6 5.6-2.7-3.7-6.1-5.5-10.6-5.5C6 3.1 0 9.6 0 17.6c0 7.3 5.4 12 10.6 16.5.6.5 1.3 1.1 1.9 1.7l2.3 2c4.4 3.9 6.6 5.9 7.6 6.5.5.3 1.1.5 1.6.5s1.1-.2 1.6-.5c1-.6 2.8-2.2 7.8-6.8l2-1.8c.7-.6 1.3-1.2 2-1.7C42.7 29.6 48 25 48 17.6c0-8-6-14.5-13.4-14.5z”></path></svg>
I’m needing to grab area-label=”Unlike” but can’t figure out how. I’ve tried the following:
browser.find_element_by_xpath(“//svg[@class=’_8-yf5 ”][@aria-label=’Unlike’]”)
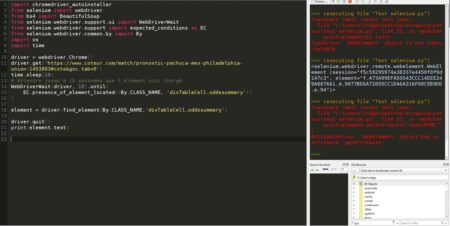
I’m using Python 3.11.5, and I want to extract text from a Webelement with selenium.
I use Chromedriver as a driver, and I want to find an element By.CLASS_NAME
Here is my code
What happens ?
When I print (element), it gives me a Webdriver element, which I can’t read.
When I print (element.text), it gives me an error :
Retrying (Retry(total=2, connect=None, read=None, redirect=None, status=None)) after connection broken by ‘NewConnectionError(‘<urllib3.connection.HTTPConnection object at 0x000001DDFE4F0690>: Failed to establish a new connection: [WinError 10061] Aucune connexion n’a pu être établie car l’ordinateur cible l’a expressément refusée’)’: /session/0109eeaf781d2f899ee82e0fd10eac19/execute/sync
What have I tried ?
After using driver.get(url), I already tried to apply time.sleep(10)
I checked my versions of Chrome + Chromedriver
I disabled my proxy
Do you have any idea about what the problem is ?
Need to validate just the structure from response with schema file not the data values. Is it possible to do in karate?
I have just completed my first two playwright tests, but I am not sure how to optimize them.
The scenario is the following:
I log in to the system with an administrative user.
I create a new user and save the generated username and password using the following code:
// copy username and password
const username = await page.locator(‘#username0’).innerText();
const password = await page.locator(‘#passwd0’).innerText();
expect(username).not.toBeNull();
expect(username).not.toBeUndefined();
expect(password).not.toBeNull();
expect(password).not.toBeUndefined();
I log out the admin user.
I log in the created user (using the const created above), accept the terms and conditions and answer 220 questions, saving a screenshot of every 20th question.
for (let x = 1; x <= 220; x++) {
if (x % 20 === 0) {
await storeScreenshot(popupPage, testInfo, ‘test Q’ + x);
}
await popupPage.waitForLoadState();
await popupPage.locator(user.selector).click();
if (x % 20 === 0) {
await storeScreenshot(popupPage, testInfo, ‘test Q’ + x + ‘ – selected’);
}
await popupPage.locator(‘#submitknap’).click();
}
I am very happy that this works, and it is even parameterized with a csv for testing different answer patterns.
If any step in this fails, the whole case fails.
Ideally the admin part is not necessary as a part of the test and is reusable, but creating a user IS something I want to have. I could create some static users and wipe them before running each test, but I like the dynamic approach of creating a user prior to logging it in. I also have some environments that are not easily reset.
I am in doubt as to how I can split this test scenario up. Should I have the admin part as a helper function called by the testcase, or as a smaller testcase prior to calling the main testcase?
Edit
For a little perspective this test takes 3 minutes to complete. a complete run of 6 parameters in three browsers takes 16 minutes.
Hyperautomation in P&C insurance is transforming the industry by integrating AI, ML, and RPA to streamline operations and enhance customer service. The blog discusses how by automating processes and decision-making, insurers can significantly reduce errors, improve processing times, and meet evolving customer expectations. This approach not only boosts operational efficiency but also ensures compliance with regulatory standards, making it essential for insurers to stay competitive in today’s challenging market.
The post Why is Hyperautomation for the P&C Insurance Industry Important? first appeared on TestingXperts.
AI has taken over many global industries, including software testing. Today, software testers can leverage this innovative technology to boost their workflow and efficiency. If you are interested in software testing or are looking for a career in this field, then you might be interested in the contemporary uses of AI, especially in connection to…
The post Understanding the Integration of AI in Software Testing appeared first on Software Testing Material.
A collection of templates, components and examples to create beautiful, high-converting landing pages with React and Next.js. The post Landing…
I’m currently building a testing framework for functional tests. I can run them in parallel using Cucumber but I have run into a problem in creating users for each thread (each test requires a brand new user).
I have a user.properties file with details for each new user created. Duplication doesn’t matter for most fields and my emails are different each time because I use something like this “useremail” + System.currentTimeMillis + “@example.com”.
My problem arises when reusing phone numbers. It needs to be a valid phone number and cannot be duplicated across accounts. I tear down users with the phone number at the beginning of each test. But running over multiple threads causes clashes of numbers.
I have 2 stored numbers in my user.properties which I hope to cycle through using a synchronized method for each thread and lock that number to that thread. But I aim to have more than 2 threads (as many phones that I can attach to be honest).
Every solution I come up with feels hacky and I’m quite new to this. Does anyone know of a good solution to distribute a finite number of user properties across multiple threads so they don’t clash?
Thought of using the actual device or emulator’s number (not sure if appium can extract that), but even if I could, my numbers need to be UK numbers
Thanks for your help.
I am developing a Selenium Test Automation Framework for the purpose of testing multiple websites.
I have currently set up the Framework in Visual Studio using C# and implementing the Page Object Model.
The Framework itself is a C# project and the Test project is separate but references the Framework.
I am happy with the fundamentals of the Framework but I want to implement some Data Driven aspects in order to increase the durability of the tests. I currently have NUnit running paramaterised test using [TestCase] but the data is hardcoded by me.
The ideal scenario would be to add a DatabaseHelper class to the Framework which would allow me to define queries on the database under test to return values and Nunit would repeat the same test for each row of the SQL query.
Has anyone here implemented a similar method and how would you go about creating it?
Moonshine is an open-source package for Laravel offering an admin panel you can use for MVPs, back-office applications, and content…
I have a result file of Concurrency Thread Group test of 500 users.
The file has aproximetly 58K rows and 16Mb
1) I tried generating a report through “Tool > Generate html report” but get time-out exception, I have increased the timer to 480000 but the result was the same.
2) I tried generate report through cmd -> it was running for a few hours and again no result, no report, all logs files have no exceptions.
Is there limitation of a report’s rows?
please help!
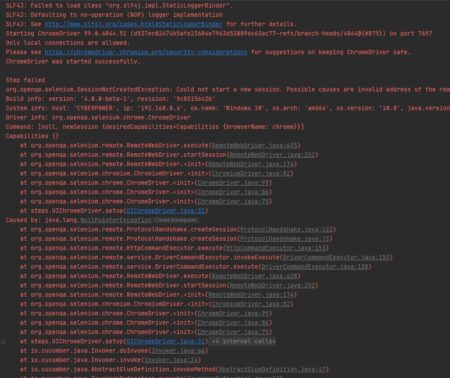
So I am trying to write a test in which the first step is logging in, but it is denying me access as it detected automation tools because the javascript has not been enabled and there is no profile. So I am trying to load my default profile. The problem I’m getting is that the browser does open, but it quickly fails as I get a SessionNotCreatedException. The failure occurs in the service hooks:
@Before(“@FrontendTest”)
public void setup() {
System.setProperty(“webdriver.chrome.driver”,
“E:\interview_notcodegod\src\drivers\chromedriver.exe” );
ChromeOptions options = new ChromeOptions();
options.addArguments(“–enable-javascript”);
options.addArguments(“–user-data-dir=C:/Users/[username]/AppData/Local/Google/Chrome/User Data”);
WebDriverManager.chromedriver().setup();
driver = new ChromeDriver(options); // intellij points here (nullpointerexception)
driver.manage().window().maximize();
}
Is there a line of code that i’m missing? I’ve updated my chromedriver already because I thought that was the issue (chrome Version 99.0.4844.74 (Official Build) (64-bit), chromedriver:99.0.4844.51)
I’m trying to code using UFT to handle privacy error pages. When i tried to scan this page using UFT, unable to recognise inner links and button. Its showing chrome legacy window.
So i thought of going with vb code. Can anyone help me in coding here which works in uft?
I am planning to build a self-heal tool to update the locators automatically when developer the changes the UI locators
Is there is an open source to check the mobile application in the Safari browser?
Right now am using Responsive Web Design tester Add on chrome but in the add on we have some devices like iPhone and Ipad but it is running under the chrome browser.
During testing the same application in the Responsive Web Design tester is working as we expected but whenever testing in Ipad my test is failed and application is behaving wrongly while displaying the dashboard data
Can anyone please suggest me to any open source tool to check in Safari browser.
Windows support for NativePHP was announced, which means that you can now build applications for the Windows platform. Windows builds are working,…