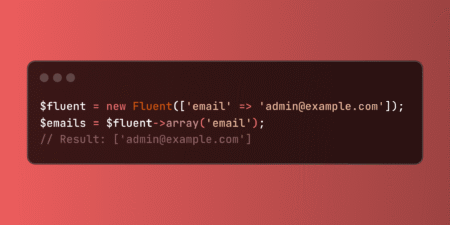
Laravel’s Fluent array() method ensures consistent array output from Fluent objects, eliminating manual casting needs. This feature simplifies configuration handling…
The Laravel team released v12.15.0, with Locale-aware number parsing, a string `hash()` helper method, inject contextual attribute values, and more.…
The SMIL specification was introduced by the W3C in 1998 for synchronizing multimedia. This was long before CSS animations or…
React vs Angular: Which Developer Should You Hire? Page Updated On GET A FREE QUOTE In today’s fast-paced digital world,…
Starting May 15, the Netherlands has introduced a new law that broadens the definition of espionage and introduces stricter penalties…
Two high-severity security flaws have been identified in Multer, a popular middleware used in Node.js applications for handling file uploads.…
Google has announced a new feature in its Chrome browser that lets its built-in Password Manager automatically change a user’s…
Cybersecurity researchers have discovered a new campaign that employs malicious JavaScript injections to redirect site visitors on mobile devices to…
Indian Ministry of Home Affairs (MHA) has introduced the e-Zero FIR system, a digital-forward solution to ensure justice for victims…
Kettering Health, a major healthcare provider in Ohio, is currently facing a widespread technology outage due to a cybersecurity incident…
It takes just one email to compromise an entire system. A single well-crafted message can bypass filters, trick employees, and…
Continuous Integration and Continuous Delivery/Deployment (CI/CD) refers to practices that automate how code is developed and released to different environments.…
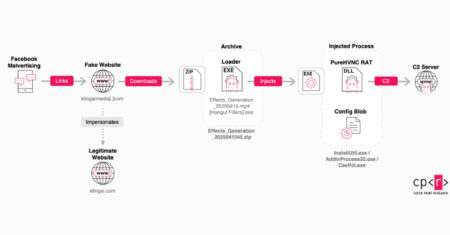
Counterfeit Facebook pages and sponsored ads on the social media platform are being employed to direct users to fake websites…
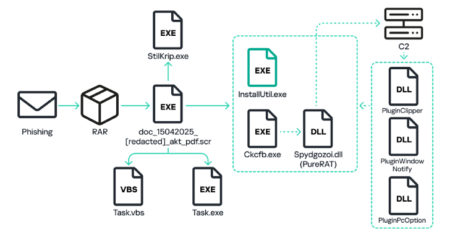
Russian organizations have become the target of a phishing campaign that distributes malware called PureRAT, according to new findings from…
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ
Post Content Source: Read MoreÂ