- Brief History of Cyber Extortion
- Cyber Extortion Timeline
- How does Cyber Extortion Work?
- Types of Cyber Extortion
- Real-world Examples of Cyber Extortion Attack
- Best Practices to Protect Yourself from Cyber Extortion
- How Tx Can Help Mitigate Cyber Extortion Risks?
- Summary
The tech space and digital business era witnessed a sudden and concerning rise in cyber-attacks in the 2024 Q3. On average, 1,876 cyber-attacks per enterprise were recorded, 75% more than the 2023 Q3 data. If we talk about which industry was primarily affected, the education/research sector would top the list with 3,828 attacks per week, followed by military/government (2,553 attacks per week) and healthcare sectors (2434 attacks per week). Talking about persistent threats like cyber extortion or ransomware attacks, over 1230 such incidents were reported, while North America led with 57% of incidents, followed by Europe with 24%. [Source: Check Point]Â
The severe cyber extortion and attacks in Q3 2024 are a stark reminder of the rapidly advancing cyber threat ecosystem. If businesses want to function correctly, they must prioritize upgrading their cyber defenses and adopt a culture of resilience. In this blog, we will learn in-depth about cyber extortion and how businesses can protect themselves from these attacks. Â
Brief History of Cyber Extortion

Before discussing cyber extortion’s history, let’s understand it. Cyber extortion is a crime in which a threat actor steals sensitive or crucial information about someone and demands money or other requirements in exchange for returning it. Another name is ransomware, in which cyber criminals leverage digital mode to extort data or money from organizations/individuals/government entities. Recently, financial exchanges are happening in the form of cryptocurrency, which has also increased cyber extortion cases over the last couple of years. Â
To understand it better, let’s take the example of an ABC company, which uses a confidential password, 123XYZ, to keep its customers’ data safe on-premises or in the cloud. A group of cybercriminals stole that password using hacking tools and techniques. Now, they will contact the ABC company to demand money or other requirements in exchange for the password and data. And that’s how cyber extortion works in the real world. Â
Cyber Extortion Timeline
| Year | Event | Description |
| 1989 | AIDS Trojan (PC Cyborg Virus) | It was the first known ransomware attack in which users were locked out of their systems until they paid $189. |
| The early 2000s | Rise of Distributed Denial-of-Service (DDoS) Extortion | Cybercriminals began launching DDoS attacks and demanded ransoms to stop the attacks. |
| 2006 | GPcode Ransomware | One of the earliest encryption-based ransomwares, encrypting files and demanding payment for keys. |
| 2013 | CryptoLocker Ransomware | Transformed ransomware by encrypting files while criminals demanded payment in Bitcoin. |
| 2017 | WannaCry Ransomware | Global ransomware attack affecting over 230,000 computers, exploiting a vulnerability in Windows. |
| 2019 | Sodinokibi (REvil) Ransomware | A highly advanced ransomware attack that targeted businesses and critical infrastructure. |
| 2020 | Maze Ransomware | Combined ransomware with data theft, threatening to leak sensitive data if ransom wasn’t paid. |
| 2021 | Colonial Pipeline Attack | A ransomware attack on a US oil pipeline operator led to fuel shortages until the ransom was paid. |
| 2023 | Ransomware as a Service (Raas) | The emergence of ransomware criminal groups offering services to less skilled attackers for a share of ransom. |
How does Cyber Extortion Work?
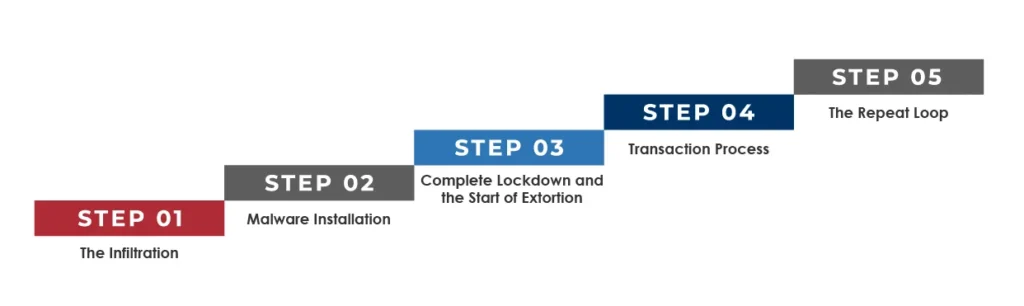
There’s a pattern in which cyber extortion operates, which varies based on tools, techniques, procedures, and tactics used by criminals. To understand how it works, let’s take a look at the steps involved:Â
Step-1: The Infiltration:
In the initial step, hackers compromise the victim’s system, data, or network using various infiltration methods. Their approach might involve phishing techniques to trick victims into disclosing critical data, which they can leverage to ask Ransome later. Another approach will be to exploit loopholes in an enterprise’s hardware, software, or vulnerabilities in human factors to gain unauthorized access to sensitive information.Â
Step-2 Malware Installation:
Once the hackers are inside the system, they install ransomware to encrypt the victim’s data. They can also spread the malware throughout the network to infect multiple devices and systems, maximizing the negative impact.Â
Step-3 Complete Lockdown and the Start of Extortion:
After gaining complete control over the victim’s system or data, the cybercriminals will take the next step, i.e., send a ransom request. When the victim realizes their data has been stolen or encrypted, they will receive a ransom note demanding money or other requirements in exchange for the decryption key. Â
Step-4 Transaction Process:
Although not advised by the law, if the victim chooses to pay, the cybercriminal will provide a method to recover or restore the data/system. However, there’s no surety that the attacker will follow their end of the deal. So, the best option is to consult the authorities that deal with cybercrime.Â
Step-5 The Repeat Loop:
In some cases, even though the attackers receive ransom, they will still be present in the victim’s system to repeat the attack in the future. A thorough incident response plan and system clean-up are necessary after an attack.Â
Types of Cyber Extortion
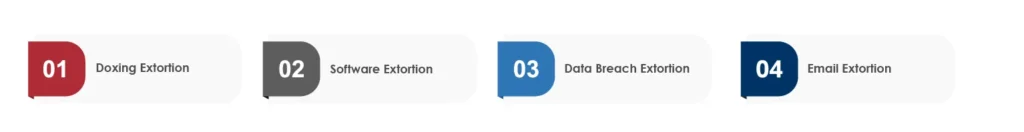
Multiple forms of cyber extortion exist, each involving unique methods and implications. Businesses must completely understand common cyber extortion types to have effective countermeasures.Â
Doxing Extortion:
In the case of doxing extortion, the attackers obtain critical/confidential/personal details about the party they plan to extort. Then, they threaten to publish or disclose the details publicly if the ransom is not paid. Therefore, doxing extortion leverages reputational damage cards to force victims into fulfilling the attacker’s demands.Â
Software Extortion:
It involves exploiting vulnerabilities in a company’s software systems and threatening to publicly expose their software loopholes if the victim does not pay the ransom. The attackers extort the victim by addressing the harm they will suffer when users exploit their software vulnerabilities.Â
Data Breach Extortion:
The attackers gain unauthorized access to sensitive data on a larger scale, often involving large organizations or entities. They threaten the victim party to sell or release the stolen data (for example, business information, passwords, clients’ data, or other critical data) if their ransom demands are unmet.Â
Email Extortion:
The cybercriminal sends an email-based extortion message threatening the victim that they will release private details to family and friends or over social media if they don’t pay the ransom. Although there is a chance that the attacker is bluffing, they might have obtained sensitive emails/text messages, videos, or pictures in some situations.Â
Real-world Examples of Cyber Extortion Attack
In 2017, the “Orange Is the New Black†TV show was hit by a cyberattack. The extortionist group demanded $50,000 in exchange if the show director and producer did not want them to pre-release some of the episodes before their scheduled release date. As a result, the show’s producer had to pay the amount, but the criminals still leaked the episodes. Â
In another incident in 2023, the University of Manchester in Manchester, England, was hit by a ransomware attack. The details of more than 1 million patients were compromised as they were part of a medical research project.Â
In 2019, Baltimore experienced a heavy ransomware attack named RobbinHood, disrupting the city’s government computer systems and servers. The criminals demanded 13 bitcoins (approximately $78,280) to restore access. They threatened that if the demands were not met within 4 days, the ransom would increase, and the data would get deleted after 10 days. Ultimately, Baltimore officials spent approximately $18 million to restore the systems.Â
Best Practices to Protect Yourself from Cyber Extortion

To protect your business against cyber extortion and avoid paying hefty ransom amounts, you should follow some practices to avoid damages caused by ransomware attacks. The first practice is always to have a backup of your files and data so that when a ransomware attack hits, you can access your crucial assets to keep your business running smoothly. Businesses should properly understand their operations and know better about their critical assets that need protection. Secondly, anti-malware and firewall protection measures should always shield the software and systems from hackers’ mechanisms to execute ransomware attacks.Â
Perform a background check on each employee to determine whether they have cases regarding digital fraud. If yes, then it’s a red flag. Train your employees about DDoS attacks, phishing, spear phishing, and whale phishing attacks and how to avoid them. Include periodic drills, tabletop exercises, and training sessions in the breach management plan to ensure the employees are well aware and prepared. Always use up-to-date software tools with the latest security patches. Implement an authentication system to manage employees’ access to IT infrastructure services. Also, a cyber extortion insurance policy should be ensured to protect the business from financial fallout after a cyber-attack. Lastly, partner with a professional and experienced cybersecurity solution provider like TestingXperts (Tx) to assess whether your security measures are updated and resilient against attacks. Â
How Tx Can Help Mitigate Cyber Extortion Risks?
The Level of safety of your IT infrastructure depends on various factors, such as your business nature, the type of data you handle, and the quality of your current cybersecurity measures. Partnering with Tx will help you tackle security risks that might lead to cyber extortion. Here’s how Tx can help:Â
- Proactive Vulnerability Assessment: Our experts will identify security vulnerabilities in your software systems that cybercriminals can exploit. We conduct regular vulnerability assessments to prevent potential attack vectors, which is vital in the current digital business environment. Â
- Penetration or Pen Testing: We launch a simulated attack to uncover weaknesses in IT security defenses. Pen testing helps identify vulnerabilities that attackers can leverage for extortion later. Â
- Conduct Security Testing and Compliance Audits: Our team can assist you in conducting compliance audits to evaluate your organization’s security posture and ensure you adhere to industry standards and regulations like GDPR, WCAG, etc. We conduct rigorous security testing to help you identify gaps in security controls that might increase extortion risks. This would help you avoid fines and penalties that could exacerbate the impact of a cyber extortion attack. Â
- Incident Response Testing: Businesses should have a well-defined incident response or disaster recovery plan. We conduct incident response testing to assess your organization’s preparedness for handling cyber extortion attacks.Â
Summary
Cyber extortion severely threatens organizations in the modern digital age. It targets critical data and leverages advanced techniques like ransomware and doxing to demand ransom. Cybercriminals exploit system weaknesses and human errors, often encrypting data or threatening to release sensitive information. To mitigate these risks, businesses must adopt comprehensive cybersecurity strategies, including vulnerability assessments, compliance audits, and incident response testing. Â
Partnering with a professional cybersecurity provider like TestingXperts (Tx) enables organizations to fortify their defenses through penetration testing and proactive security monitoring, ensuring robust protection against potential extortion threats. Contact our experts to learn how Tx can help.Â
The post Cyber Extortion: Protecting Your Business from Digital Blackmail first appeared on TestingXperts.
Source: Read More



