Security researchers have found a trove of threat actor tools that can bypass security defenses like Windows Defender and Malwarebytes, delete backups, disable systems, and many more malicious processes.
The threat actors are using tools like SLiver, Ngrok, SystemBC and PoshC2 to communicate with their Command-and-control (C2) servers. The tools have likely been used in ransomware intrusions in a campaign that dates to at least September 2023, and activity has continued into August 2024.
Threat Actor Tools Found in Open Directory
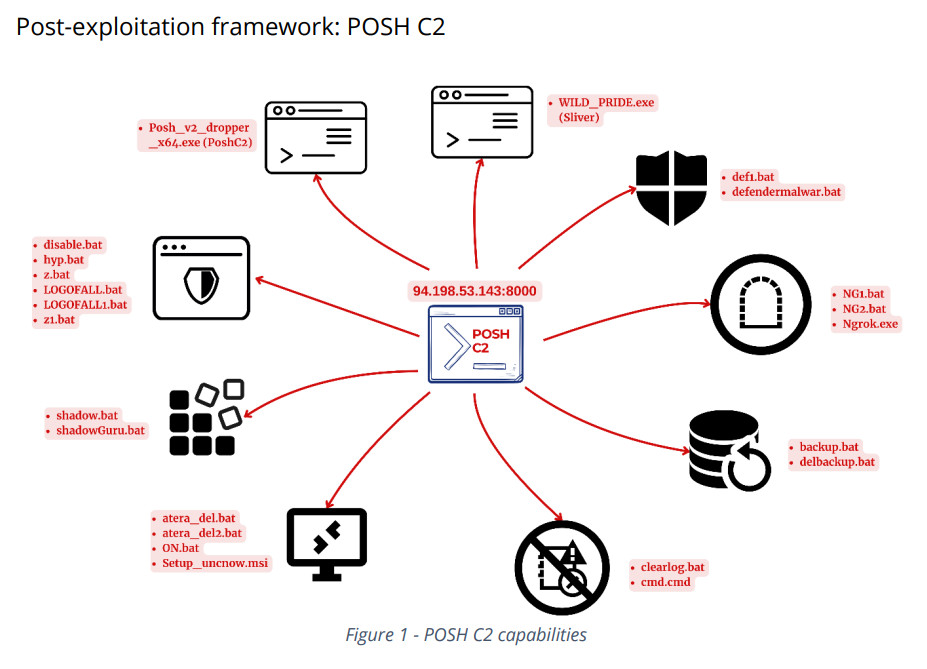
In December 2023, DFIR threat researchers discovered an open directory containing batch scripts designed for defense evasion and executing command and control (C2) payloads, deleting backups, and disabling SQL, Hyper-V, antivirus tools, and Exchange servers.
Their investigation also revealed the use of tools like Ngrok, SystemBC, and C2 frameworks Sliver and PoshC2. The tools have likely been developed for ransomware intrusion activities. The threat actors have been active since September 2023, with the latest activity observed in August 2024.
The open directory contains a wide range of batch scripts, each crafted for different stages of an attack and aimed at both Windows and Linux systems. These scripts are integral to the attacker’s operations, performing tasks such as disabling security measures, stopping critical services, and establishing command and control channels.
Scripts Developed for Three Attack Phases
In an analysis of the findings, Cyble threat researchers broke down the scripts into three attack phases:
Defense Evasion: These batch scripts are designed to disable endpoint security and antivirus software, making it easier for attackers to avoid detection. This includes terminating processes associated with antivirus tools and stopping security-related services, such as those related to SQL, Hyper-V, and Exchange servers.
Persistence and Privilege Escalation: Some scripts are aimed at gaining and maintaining elevated privileges within the compromised environment. This includes deleting backups, wiping event logs, and managing the installation or removal of remote monitoring (RMM) tools like Atera, which could be used for continued access and control.
Command and Control: The scripts also set up and maintain communication channels with the attacker’s C2 servers. Tools like Ngrok and SystemBC and well-known frameworks such as Sliver and PoshC2 are employed to tunnel traffic, relay commands, and exfiltrate data, ensuring ongoing control over the compromised systems.
Cyble researchers said that “By analyzing these scripts in detail, we can better understand the attacker’s strategy and the specific techniques they employ to execute, sustain, and conceal their operations across various stages of their attack campaign.â€
Here are the scripts, 24 in all:
File Name
Description
atera_del.bat / atera_del2.bat
Removes Atera remote management agent
backup.bat
Deletes all system state and general backups, removes all shadow copies, and ignores all boot failures
clearlog.bat
Deletes Windows event logs, clears recycle bin, and removes registry keys related to the terminal server client
cmd.cmd
Disables UAC and modifies registry settings, including RDP settings
defendermalwar.bat
Disables Windows Defender, alters user account control settings and uninstalls Malwarebytes
delbackup.bat
Deletes all system state backups, backup catalogs, shadow copies, and alters boot configuration to ignore failures
disable.bat
Stops and disables services related to Microsoft SQL and Exchange, various database services, and additional system services
hyp.bat
Deletes various Hyper-V, SQL, and Firebird server services; stops a wide range of system and third-party services on Windows machines
LOGOFALL.bat
Lists all user sessions and logs off each session except the first one
LOGOFALL1.bat
Attempts to log off all sessions up to the 20th session, excluding the current user’s session
NG1.bat
Contains a Ngrok authentication token that runs on port 3389 (RDP)
NG2.bat
Contains a Ngrok authentication token that also runs on port 3389 (RDP)
Ngrok.exe
Legitimate tool abused for proxy purposes
ON.bat
Ensures network services are running and set to start automatically
Posh_v2_dropper_x64.e xe
PoshC2 dropper, a PowerShell-based C2 executable
native_dropper
Linux version of Posh_v2_dropper_x64.exe
poshc2+user.txt
Text file with PowerShell one-liners to execute the PoshC2 agent and perform further post-exploitation actions
py_dropper.sh
Bash shell script to execute a Python dropper for PoshC2
Setup_uncnow.msi
Atera remote admin tool installer
shadow.bat / shadowGuru.bat
Deletes multiple registry keys related to security tools and creates network shares with full access permissions for multiple disk drives
VmManagedSetup.exe
SystemBC malware executable
WILD_PRIDE.exe
Sliver C2 framework executable
z.bat
Removes services and processes associated with Hyper-V, multiple AV programs, SQL, and other specific services
z1.bat
Automates disabling of processes, services, registry modification, and other defense evasion techniques
Indicators of Compromise and MITRE ATT&CK Techniques Observed
Below are the indicators of compromise (IoCs) and MITRE ATT&CK techniques observed in the PoshC2 threat actors’ arsenal.
Source: Read More