AWS Database Migration Service (AWS DMS) helps you migrate your databases to AWS in a secure and efficient way. AWS DMS supports moving databases between different platforms, such as from an on-premises SAP ASE (formerly known as Sybase ASE) to Amazon Relational Database Service (Amazon RDS) or Amazon Aurora engines.
In this post, we walk you through how to configure Secure Sockets Layer (SSL) encryption between the source endpoints in AWS DMS and an on-premises SAP ASE source for secure data transfer. We also show you the steps for enabling SSL on an on-premises SAP ASE database. Configuring SSL encryption on source endpoints enables encrypting data in transit during the database migration process for enhanced security.
Solution overview
To secure data in transit when migrating from an on-premises SAP ASE database to the AWS Cloud using AWS DMS, you generate certificates using OpenSSL and import them into the source database and AWS DMS. For this use case, you configure AWS DMS to use SSL for the source endpoint, and test connectivity over SSL. You use AWS Secrets Manager to store database credentials.
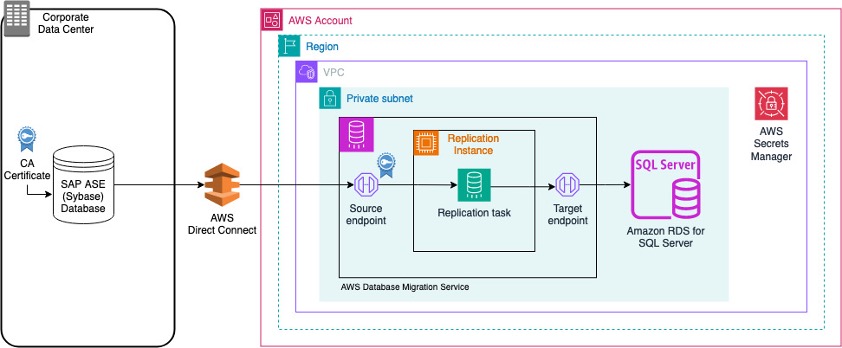
The following diagram illustrates this solution’s architecture.
The architecture consists of the following main components:
A source on-premise SAP ASE database.
AWS DMS components (source endpoint, replication instance, target endpoint) in a VPC
A target Amazon RDS for SQL Server database in a VPC
The solution contains the following steps:
Generate SSL certificates with OpenSSL on an SAP ASE instance.
Configure the certificate authority (CA) certificate on the SAP ASE database.
Configure the source SAP ASE database endpoint with SSL on the AWS DMS console.
Test and troubleshoot the source endpoint connection.
Prerequisites
To get started, you must have the following prerequisites:
An active AWS account
SAP ASE installed and OpenSSL installed (We are using EC2 instance with SAP ASE installed and OpenSSL installed for this blog post)
An SAP ASE login with sa role permission
An AWS DMS replication instance
Generate SSL Certificates with OpenSSL on an SAP ASE instance
To create your own self-signed certificate, you need to connect to an instance where OpenSSL is installed. In this post, you use SAP ASE hosted on an EC2 instance and OpenSSL installed. Complete the following steps:
Generate a private key using the following command:
The following screenshot shows SAP_ASE_SERVER-key.pem is generated.
Generate the self-signed certificate using the following command:
The following screenshot shows the SAP_ASE_SERVER-cert.pem certificate file is generated. Enter the input parameters of your choice while running the command:
The Common Name (CN) of the subject certificate must match the exact case of the server name in the interfaces file. For this post, you use the CN as SAP_ASE_SERVER because the SAP ASE server name used in this demonstration is SAP_ASE_SERVER.
To convert the certificate and key to a .pfx file, run the following command and provide a password when prompted:
You use the same password later to export the certificate file.
The following screenshot shows that the SAP_ASE_SERVER.pfx file is generated.
To convert the .pfx file back to a .pem file, which contains the certificate and key, run the following command and enter the password you used earlier when prompted:
The following screenshot shows that the root certificate file SAP_ASE_SERVER.pem is generated.
Configure the CA certificate on the SAP ASE database
In this post, the SAP ASE source database server name is SAP_ASE_SERVER, so you name the root certificate SAP_ASE_SERVER.pem. Complete the following steps to configure the CA certificate:
Copy this root certificate to the SAP ASE installation directory:
The following screenshot shows the root certificate copied to the SAP ASE certificate installation path (/opt/sap/ASE-16_0/certificates/).
Log in to the SAP ASE database server with system administrator (sa) access login to enable SSL at the database server and add the certificate to the SAP ASE database, using the following SQL command. You can use isql or any other database client tool to access the database. Use the certificate file import password (<cert-password>).
The following screenshot shows the SQL commands were run using isql to modify the database configuration and add the certificate file.
When the configuration changes are complete, shut down the database server for the configuration changes to take effect.
In the SAP ASE database, the trusted roots file maintains a list of known and trusted CAs. This file has a similar format to a certificate file, but it only contains certificates for CAs that are trusted by client applications, servers, network resources, and so on.
Copy the content of the root certificate to the trusted.txt file:
Modify the SAP ASE interfaces file (/opt/sap/interfaces) to add the SSL security mechanism as a filter on the master and query lines:
Start the database server after you complete the preceding steps.
Configure the source SAP ASE database endpoint with SSL
To set up your source endpoint, you need to import the certificate (<server-cert>.pem) you created into AWS DMS. To import the certificate, complete the following steps:
On the AWS DMS console, choose Certificates in the navigation pane.
Choose Import certificate.
For Certificate identifier, enter a name (for example, SAPSSLCERT).
For Import certificate file, choose Choose file to browse your files.
Locate SAP_ASE_SERVER-cert.pem on your local machine.
Choose Import certificate to add a new CA certificate.
When the certificate is imported successfully, you can see it listed as shown in the following screenshot.
The next step is to configure the source endpoint with SSL mode enabled as verify-ca.
On the AWS DMS console, choose Endpoints in the navigation pane.
Choose Create endpoint.
For Endpoint type select Source endpoint.
Enter a name for your endpoint (for example, sap-ase-source) and an optional Amazon Resource Name (ARN).
For Source engine, choose SAP Sybase ASE.
For Access to endpoint database, select your preferred method of authentication to the SAP ASE source: Secrets Manager or manual authentication. For this post, we select AWS Secrets Manager.
For Secret ID, create a secret for the SAP ASE database in Secrets Manager or use an existing secret ARN. You can use below secret attribute keys and values specific to your environment or choice in secrets.
Here, db_username is the name of the user accessing the database, db_user_password is the password of the database user, db_port_number is the port number to access the database, and db_server_name is the database server name (address) on the web or an IP address.
For IAM role, create a new AWS Identity and Access Management (IAM) role or use an existing one that grants AWS DMS permission to access the secret.
For Secure Socket Layer (SSL) mode, choose verify-full.
This mode makes sure the connection to source is encrypted. It also verifies the server certificate and verifies that the server hostname matches the hostname attribute for the certificate.
SAP ASE as a source database engine only supports verify-full mode to enable SSL. For more information about compatibility for source engines and SSL modes, refer to Using SSL with AWS Database Migration Service.
For CA certificate, choose the certificate you imported (SAPSSLCERT).
For Database name, enter a database name (for example, pubs2).
Choose Create endpoint to finalize the setup of the source endpoint.
After a successful configuration, the endpoint is listed on the AWS DMS console.
Test the source endpoint connection
Now you can test the connection to the source database using the endpoint you created:
On the AWS DMS console, choose Endpoints in the navigation pane.
Select the endpoint to test (sap-ase-source).
On the Actions menu, choose Test connection.
For Replication instance, choose the replication instance to test (rep-instance-sap-ase-aod).
Choose Run test and wait for the status to be successful.
These steps validate the data migration from the on-premises SAP ASE database to the AWS Cloud using AWS DMS and data in transit encryption using SSL.
To create a target endpoint for other database engines, refer to Creating source and target endpoints.
After you have created both the source and target endpoints, refer to Working with AWS DMS tasks to create AWS DMS tasks and migrate the data.
Clean up
When you’re done testing the solution, delete the resources you created to avoid unexpected charges:
On the Amazon EC2 console, select the instance that hosts the SAP ASE database.
On the Instance state menu, choose Terminate instance.
On the AWS DMS console, in the navigation pane, choose Replication instances.
Select the instance to delete and on the Actions menu, choose Delete.
Conclusion
In this post, we demonstrated how you can set up SSL encryption for AWS DMS with an SAP ASE database as source. Enabling SSL encryption protects your database data while it is being transferred from on premises to the AWS Cloud. Using SSL helps provide compliance with your organization’s security policies and guidelines.
Consider implementing this SSL configuration in your own AWS environment. post any questions or feedback about this approach in the comments.
About the Authors
Nishad Mankar is a Lead Database Consultant with AWS Professional Services in India. He plays pivotal role in helping customers to migrate and modernize their databases on AWS cloud platform. With expertise in database technologies such as SQL Server, SAP ASE, and PostgreSQL, he builds cutting-edge solutions that helps customer success.
Jitendra Kumar is a Lead Database Migration Consultant at AWS with over 20 years of working experience in enterprise databases like Db2, SAP ASE, and SQL Server. He focuses on helping customers migrate and modernize their workloads to AWS.
Rajkumar Raghuwanshi is a Database Consultant with AWS Professional Services based out of Pune, India. With good knowledge on relational databases adding hands-on in homogenous and heterogenous database migrations, helps customers in migrating to AWS cloud and their optimizations.
Source: Read More